HackTheBox-Explore
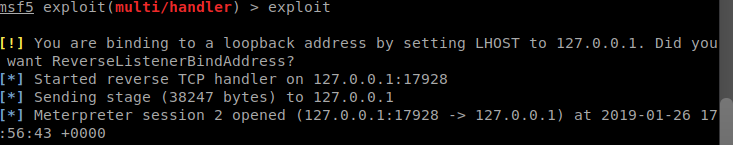
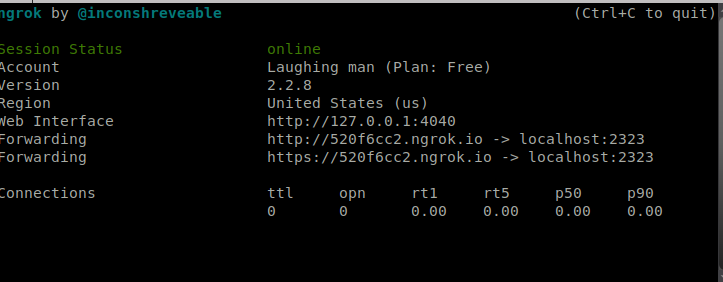
Hello everyone, this HackTheBox walkthrough ARZ101, shows you how to hack the HackTheBox-Explore machine. this write-up is related to HackTheBox Explore box which was the first android machine seen on the platform, starting with the Nmap scan we can see 4 TCP ports and an ssh port which were not common ports. On port 42135 … Read more