Hacking Android Smart Phone Using AhMyth Android RAT
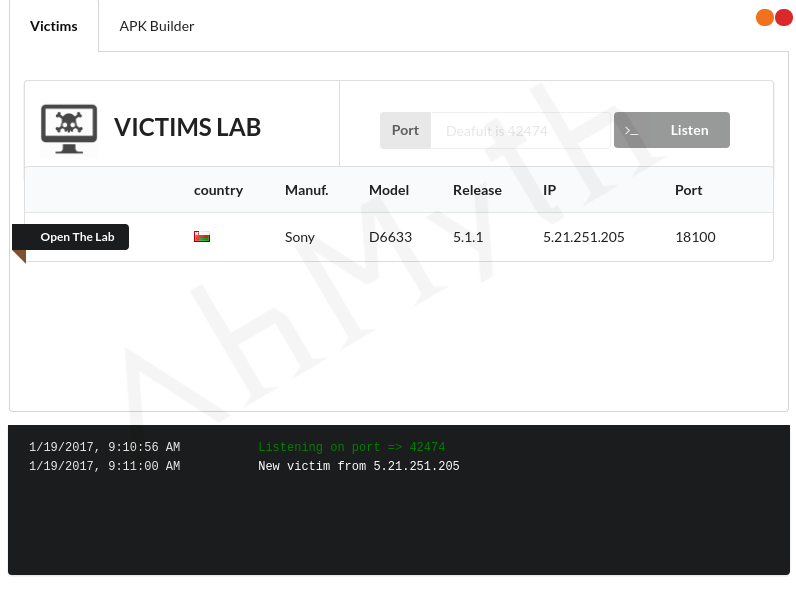
Hacking Android Smart Phone Using AhMyth Android RAT Android RAT AhMyth Hacking Tutorial: Welcome back, Today I will show you how to hack an Android smartphone to gain remote access. In this tutorial, we will be working with a tool called AhMyth an open-source remote access tool AhMyth has many features you would expect to … Read more