Explanation of Rootkits & How To Stay Safe From Rootkits
In this article I will explain what Rootkits are and how we can stay partially safe from Rootkits. For our new readers when I say partially safe is because no system is ever safe and the manner this type of software is distributed Rootkits can go unseen from users for a very long time and are sometimes never discovered.
A rootkit is a piece of software that usually comes with malicious intent. Rootkits act different to most the common viruses. This is because Rootkits are designed to leave no trace on the target system. This allows the attacker to fool the target machine and its operator into thinking the system is safe when in fact it has been compromised.
The process of using Rootkits usually involves replacing important executable system files that the Operating System needs to function correctly.
Rootkits allow Virus and Malware to hide in plain sight quite often without detection. They do this by replicating themselves as necessary system files by mimicking these system files they will quite often going undetected by anti-virus software and the system’s operator however the rootkit is self can do no harm to the system at all. This is because Rootkits are designed to hide vIrus, malware, botnet malware, worms and ransom-ware.
Rootkits can modify and edit activates within the system’s boot configuration and can often alter system files before it boots. This makes it extremely hard to detect a rootkit due to the manor they are installed and used it also makes them very difficult to remove.
To install a rootkit an attacker must gain access to the root account often by using an exploit or obtaining the password by using various hacking methods.
Rootkits today usually are not used to gain elevated access, but instead are used to mask malware payloads more efficiently.
Why is it called Rootkit? the term Rootkit originates from Linux administrator account name called “root” and “kits,” which refer to pieces of software that implement the tool.
Keeping yourself safe from Rootkits
Do not think because you have a Rootkit vulnerability scanner that you are 100% safe from Rootkits as I mentioned early in the post Rootkits main purpose is to go unseen and often for long periods of time.
Chkrootkit
Chkrootkit is a classic rootkit scanner. It checks your server for suspicious rootkit processes and checks for a list of known rootkit files.
You can install Chkrootkit by opening up a terminal and using command below.
apt-get install chkrootkit
You can even run chkrootkit by a cron job and get the results emailed to you. First, find out the path where chkrootkit is installed on your server
You can do this in Linux using which utility
which chkrootkit
Example
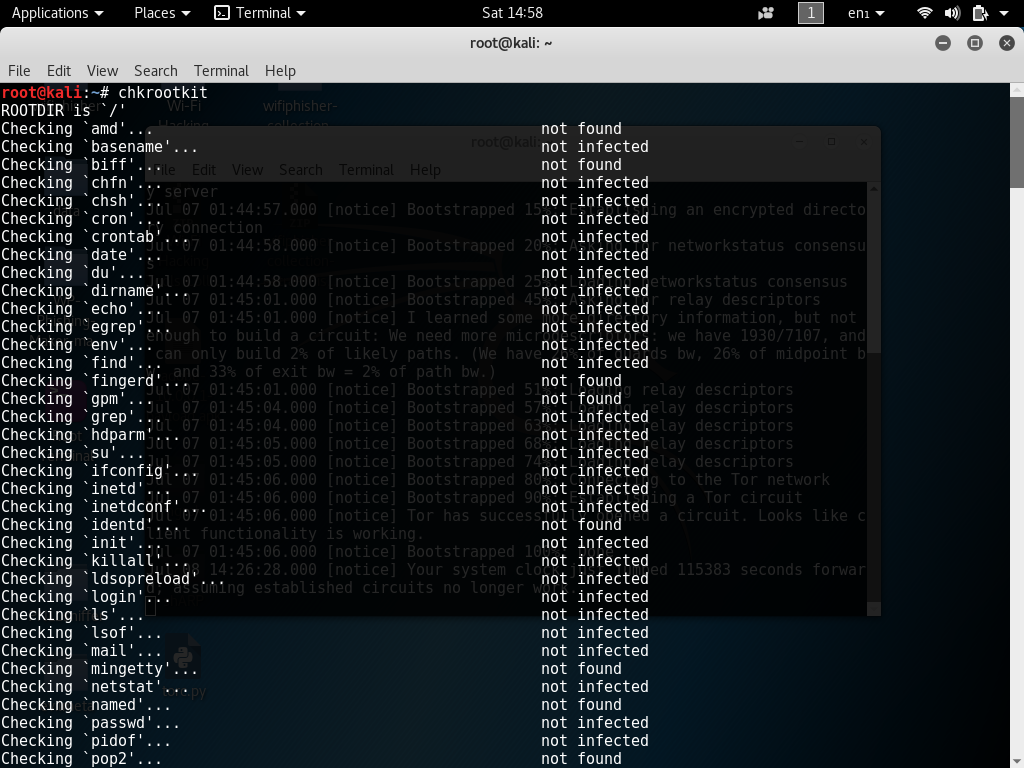
Open up a new terminal and use command chkrootkit. This will start chkrootkit and start to scan for infected files.
chkrootkit
Sending Automatic Reports
root@server1:/tmp/chkrootkit-0.50# which chkrootkit /usr/sbin/chkrootkit
Chkrootkit is installed in the path /usr/sbin/chkrootkit, we need this path in the cron line below:
Run: crontab -e
To create a cron job like this:
0 3 * * * /usr/sbin/chkrootkit 2>&1 | mail -s "chkrootkit output of my server" you@yourdomain.com)
This cron job would run chkrootkit every night at 3.00h.
Replace the path to chkrootkit with the one that you got from which command above and exchange the email address with your real address.
