Scan WordPress websites for vulnerabilities WPScan Kali Linux
WPScan is a black box vulnerability scanner for WordPress websites. WPScan comes pre-installed in Kali Linux.
Kali Linux is a popular Linux distribution built on Debian Kali Linux that comes with many of the best ethical hacking tools pre-installed. If you’re not using Kali Linux and you prefer to use another Linux distro you can install WPScan from the source.
In this tutorial, I will be using WPScan included in Kali Linux to scan our blog for known vulnerabilities.
First, we need to install WPScan if you’re using Kali Linux you can skip this step.
Install WPScan From RubyGems
gem install wpscan
Install WPScan From Source
git clone https://github.com/wpscanteam/wpscan cd wpscan/ bundle install && rake install
Scanning for vulnerabilities in WordPress websites
I will show you a few useful commands that we can use in WPScan to search for known vulnerabilities in WordPress Blogs.
Open a terminal and use commands below to launch WPScan against the target WordPress website.
Usage
wpscan --url blog.tld
Replace blog.tld with the domain you want to scan for vulnerabilities.

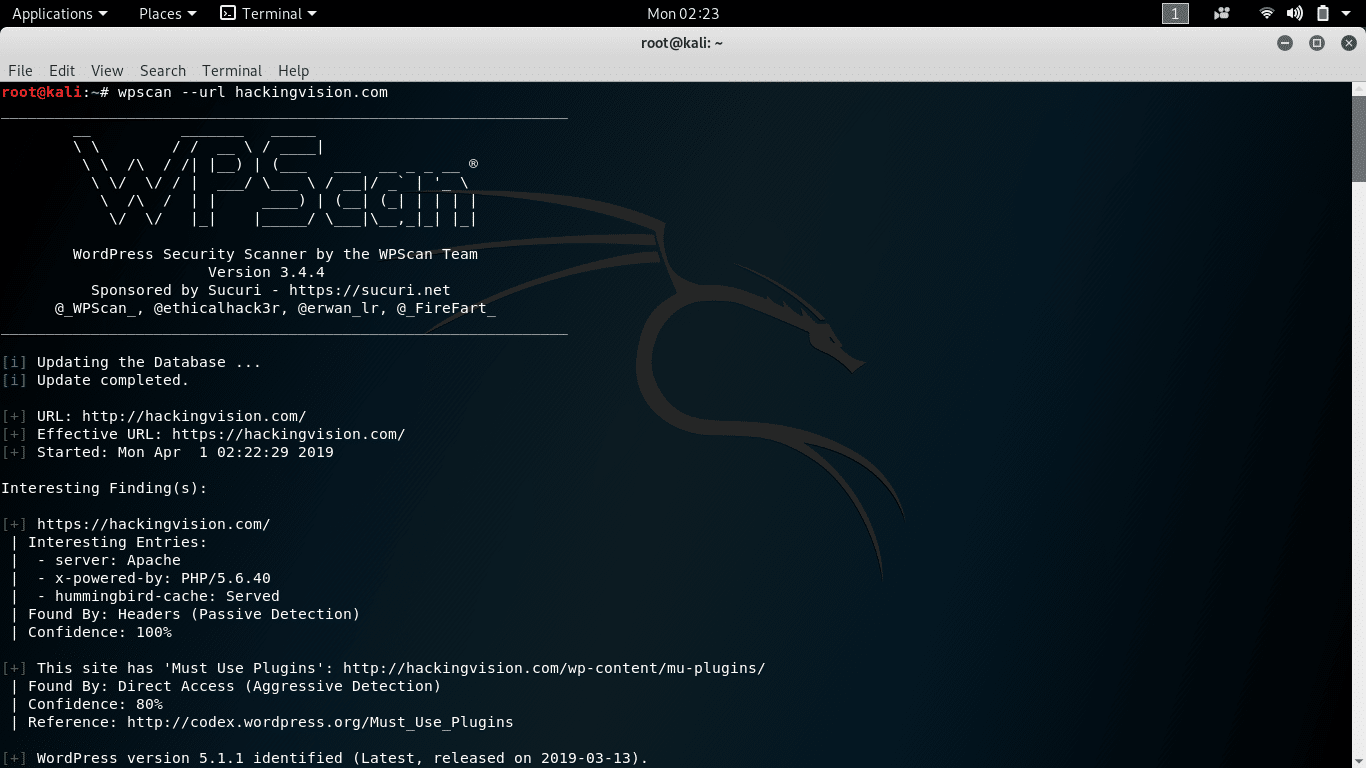
This command will scan the WordPress blog using WPScan default options the plugins will be checked passively but their version with a mixed detection mode (passively + aggressively).
If we require a more stealthy approach is then we can use command.
wpscan --stealthy --url blog.tld
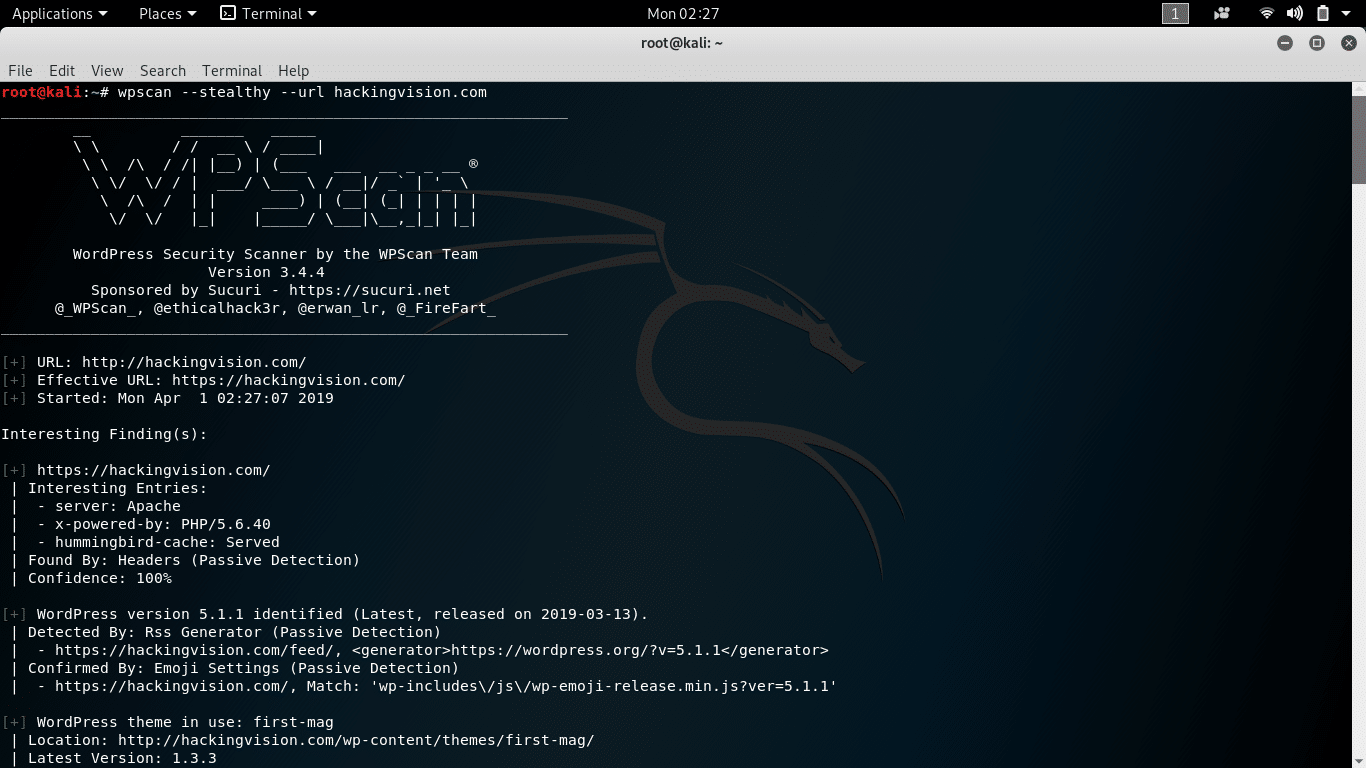
If you’re using the –enumerate option, don’t forget to set –plugins-detection as by default it is passive.
For more options.
wpscan --help
Enumerating usernames
By enumerating usernames we can find useful information such as author usernames.
wpscan --url https://hackingvision.com/ --enumerate u


Enumerating a range of usernames
By setting a range of usernames we can limit how many usernames WPScan will enumerate. wpscan --url https://hackingvision.com/ --enumerate u1-100
Replace u1-100 with a range of your choice.
Updating WPScan
We can update the WPScan local database using command.
wpscan --update
Updating WPScan itself is done by command gem update wpscan or packages manager (Important for Kali Linux).
apt-get && apt-get upgrade
Run WPScan with Tor
To preserve anonymity we can use Tor with WPScan.
If you don’t already have Tor install using command.
sudo apt-get install tor

Start Tor.
sudo service tor start

When we launch WPScan we need to include –proxy socks5 option this allows us to use Tor with WPScan.
Example
wpscan --url hackingvision.com --proxy socks5://127.0.0.1:9050

WPScan official website: https://wpscan.org/
