Cracking Wireless Router Using Aircrack-ng with crunch
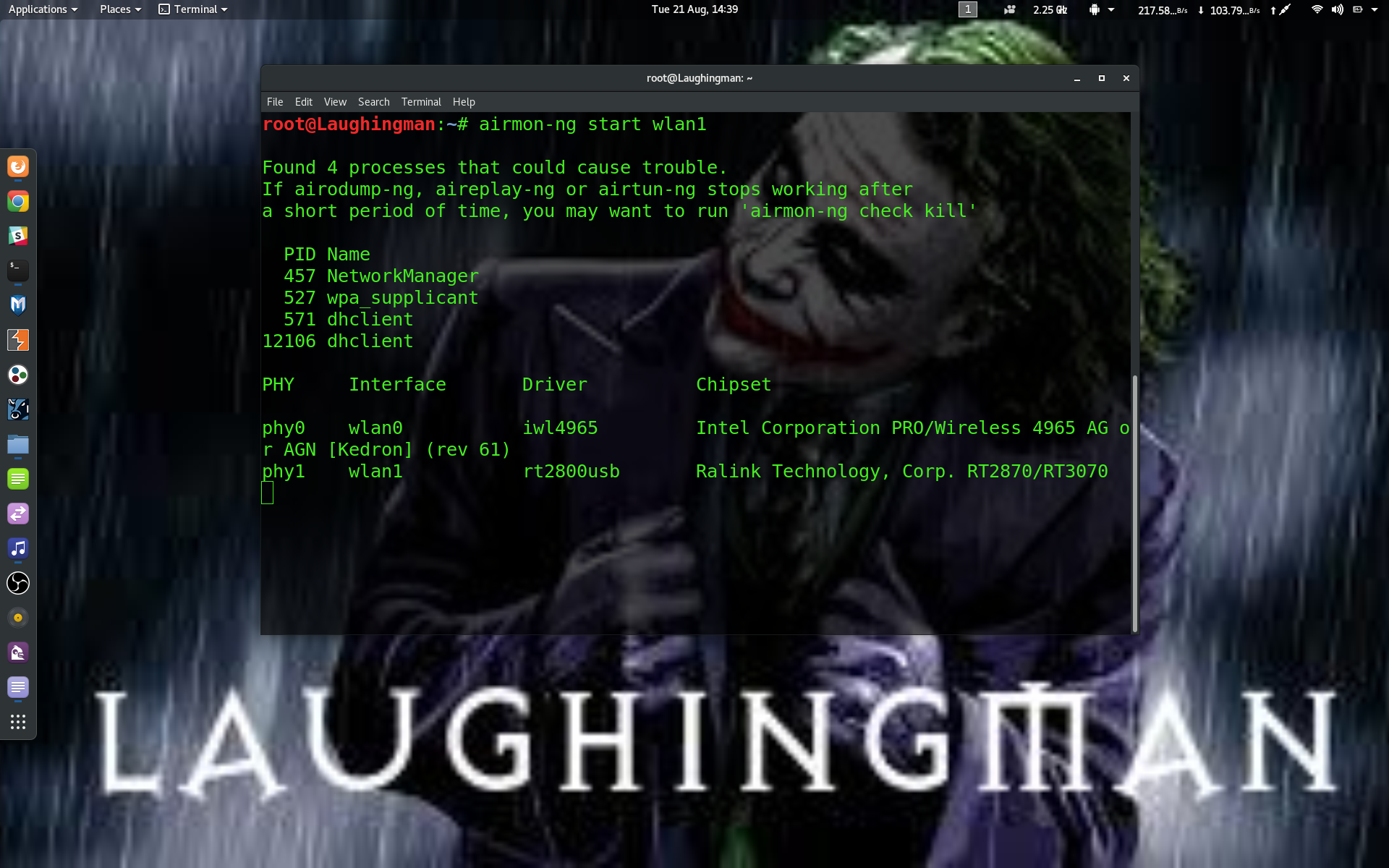
Cracking Wireless Router Using Aircrack-ng with crunch Welcome to HackingVision, today I will show you how to crack a wireless WPA/WPA2 router using Aircrack-ng and crunch. First off this is tested on my own home network. I don’t advise hacking anyone else’s WiFi but your own. First, we need to put our wireless adaptor into … Read more