VBScript Obfuscator/Defuscator in VBScript
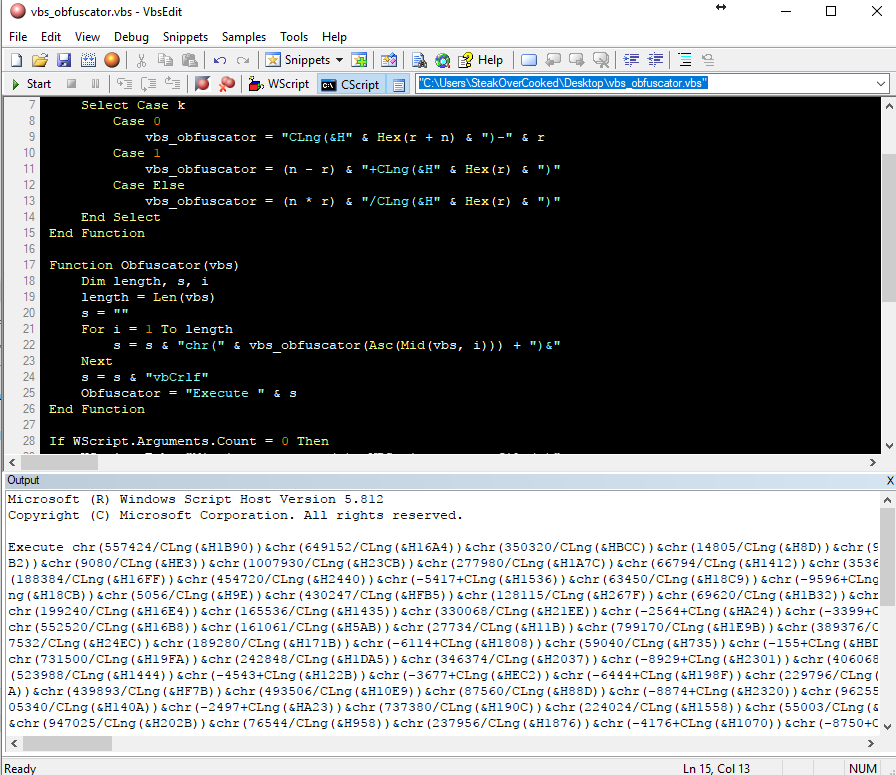
The VBScript Obfuscator written in VBScript How to Use? The command line utility is interpreted under Window Scripting Host. VBScript source files can be passed as command line parameters and the obfuscated source will be printed to console. cscript.exe vbs_obfuscator.vbs sample.vbs Defuscator in VBScript You can revert the process via vbs_defuscator.vbs cscript.exe vbs_defuscator.vbs sample_defuscated.vbs > … Read more