Relevance score 0: Android’s regular security update for December 2017 included a fix for Janus malware
With over 2 Billion active devices Android market is the biggest smartphone market and competitor of IOS devices. But these 2 Billions of devices are at a severe security risk by the detection of this newly discovered vulnerability.
The vulnerability dubbed “Janus“, allows attackers to upload a malicious code to a legitimate Android application code. The scary part is that this modification will not affect the signature verification certificates, which will eventually make it impossible to distinguish between the legitimate application and modified application.
The vulnerability (CVE-2017-13156) was reported to Google on July 31, 2017, by security firm Guard Square. Google acknowledged the very same day and released a patch for its partners in November.
Working of “Janus“
The vulnerability allows the attacker to add some extra lines of malicious code to the code of the legitimate applications without affecting the application’s signature. The vulnerability is actually the way Android handles the installation or Updates of an Android application. Usually, when an Android application installs or updates, Android checks APK header information to determine if the archive contains code in the compressed DEX files.
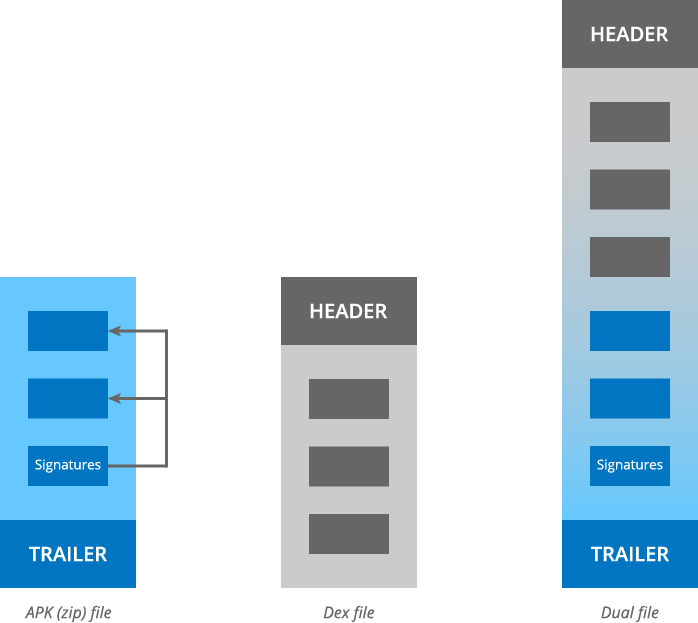
When the header information determines that archive contains a DEX file, then the system will execute the DEX file accordingly. In this case, researchers found that an apk archive can contain DEX files along with the application code.
In further explanation, researchers said “An attacker can prepend a malicious DEX file to an APK file, without affecting its signature. The Android runtime then accepts the APK file as a valid update of a legitimate earlier version of the app. However, the Dalvik VM loads the code from the injected DEX file.“
Google has released a patch for this vulnerability along with 46 other androids critical bugs, as part of its Android security bulletin December 2017.
The Scary Part
Although Google has released the security patch, in order to apply that users need to update their Android-OS. But, users for whom this option is not available still remains vulnerable. The earlier versions of Android (lesser that Nougat 7.0) which does not support APK signature scheme version 2 remains vulnerable.
Users who have no option to update the android os and install security updates on their devices can avoid getting attacked by simply not using third-party app stores to install or update their android applications.
Having Google’s AI-powered “Google play protect” enabled, Google makes sure that android play store doesn’t contain any suspicious application. It detected some spyware like Tizi Spyware. So, it is highly recommended for the users to use Google Play store to install or update their android applications.

