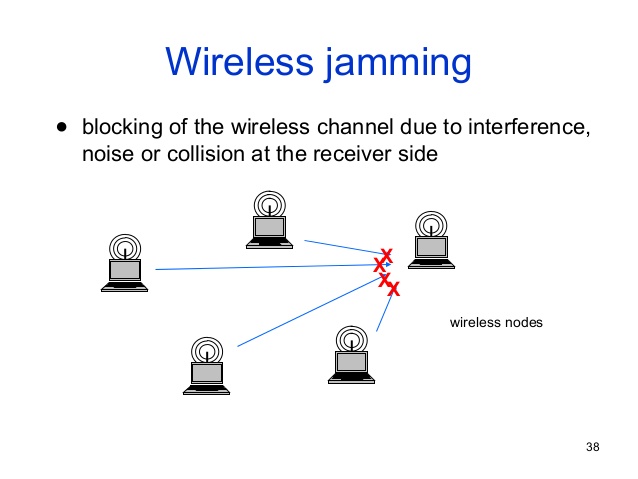
How Thieves Can Target High End Devices Using Wifi Signals
How Thieves Can Target High-End Devices Using Wifi Signals Your wireless devices could be leaking information about them selfs to hackers and criminals or anyone with a smartphone. Wifi signals Disclaimer HackingVision does not condone the illegal use of this software nor does it promote the illegal use of this software mentioned in this article. … Read more