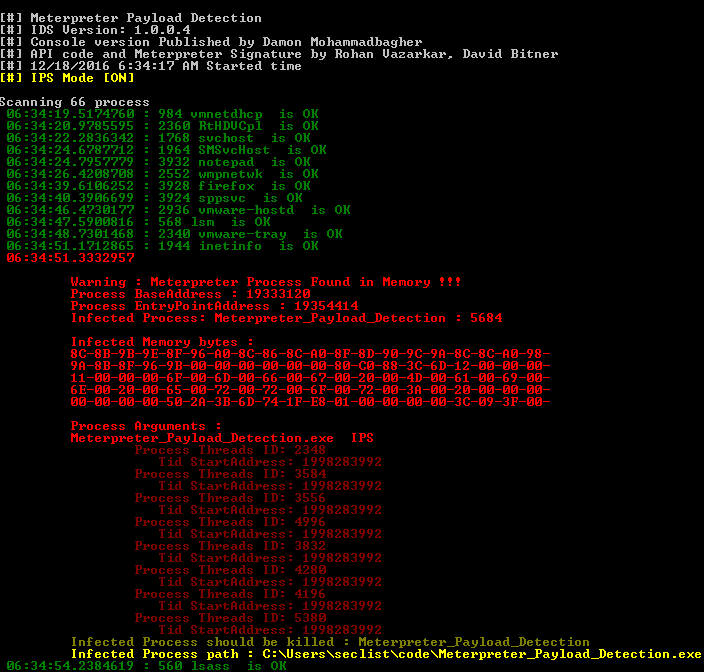
Meterpreter Payload Detection – Tool for detecting Meterpreter in memory like IPS-IDS and Forensics tool
Meterpreter_Payload_Detection.exe tool for detecting Meterpreter in memory like IPS-IDS and Forensics tool DOWNLOAD Meterpreter_Payload_Detection [sociallocker id=968]https://github.com/DamonMohammadbagher/Meterpreter_Payload_Detection[/sociallocker] CREDITS: DamonMohammadbagher Install Notes Download Meterpreter_Payload_Detection Compile C#code or unzip release_v1.0.0.4 Run Meterpreter_Payload_Detection.exe If you liked this software please consider leaving a star and folking the software from github. C# code Author : Damon Mohammadbagher Meterpreter Signature Authors : … Read more