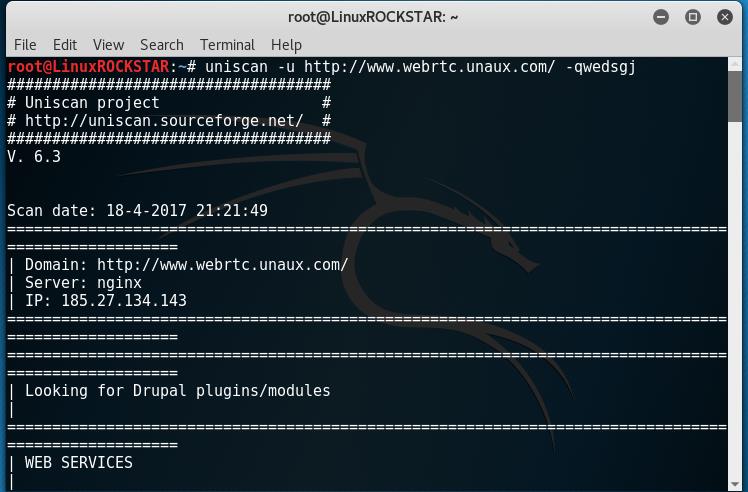
Scan website for vulnerabilities with Uniscan Kali Linux Tutorial
Scan website for vulnerabilities with Uniscan Kali Linux Tutorial Uniscan Kali Linux Tutorial: Welcome to HackingVision, in this tutorial you will learn how to scan and fingerprint a web server or device to find vulnerabilities. To achieve this we will be using a tool called Uniscan. This tutorial will require a Linux Operating system we … Read more