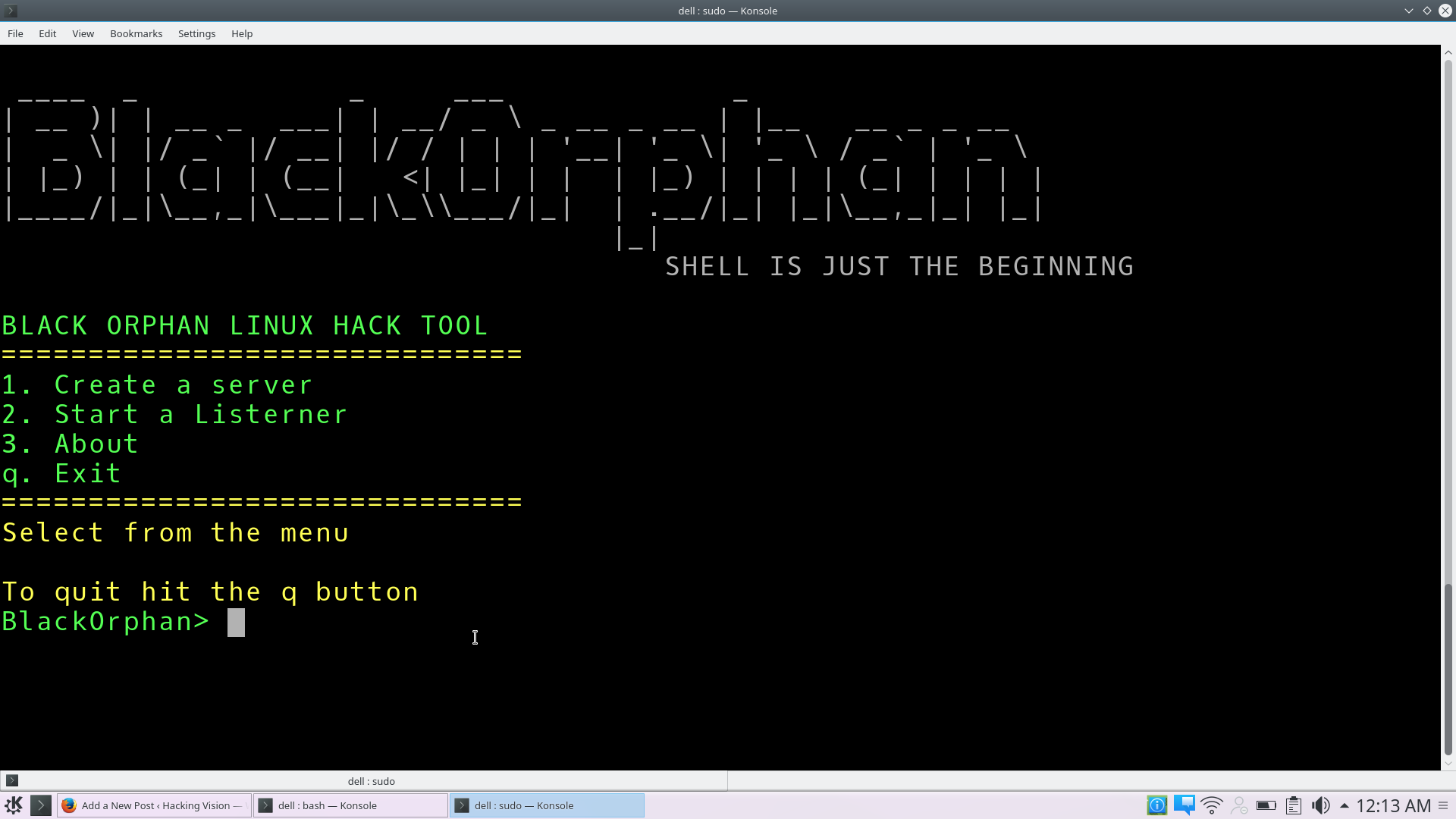
BlackOrphan – Tool built with Bash/nodeJs mainly for gaining a remote shell access to a Linux Box
BlackOrphan is a tool built with Bash/nodeJs mainly for gaining a remote shell access to a Linux Box BlackOrphan is a tool built with Bash/nodejs mainly for gaining a remote shell access to a linux BoX USAGE clone this repo git clone https://github.com/zombieleet/BlackOrphan.git run blackorphan from the command line ./BlackOrphan1.0 ============================== 1. Create a server … Read more