Phone Hackers: Britain’s Secret Surveillance
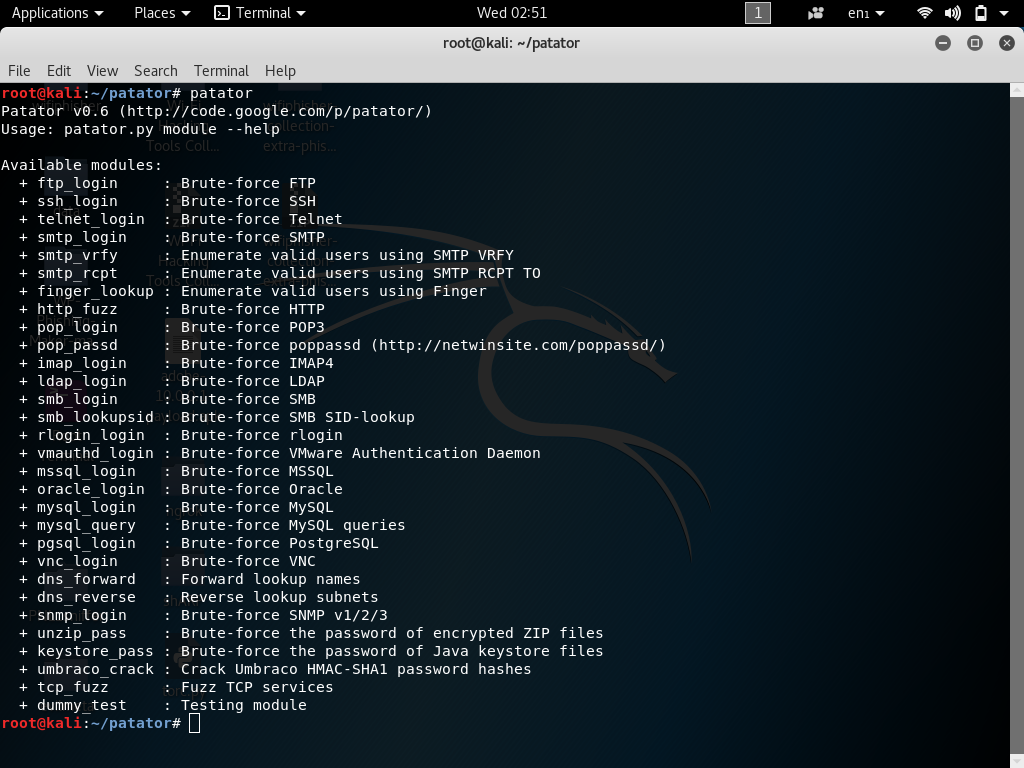
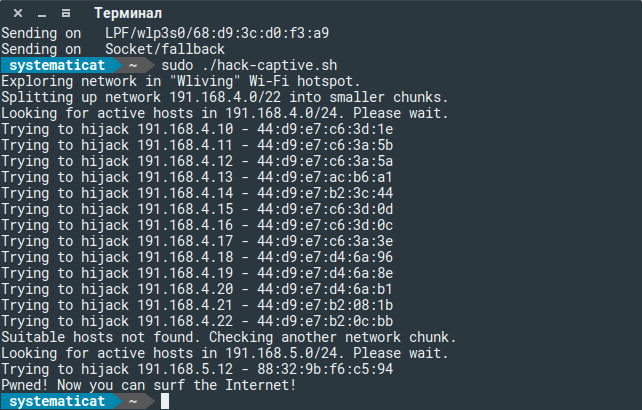
Phone Hackers: Britain’s Secret Surveillance in this video, Vice Media uncovers one of Britain’s secret surveillance devices the IMSI catcher. International Mobile Subscriber Identity-catcher, IMSI Catcher/stingray are portable devices used to hack mobile phone communications, within a set area by claiming to be a cell phone tower. IMSI Catchers allow law enforcement and government agencies to hack mobile phone communications with very little ease. In the UK (United Kingdom) we don’t know who are using IMSI catchers nor do we know their intentions. IMSI Catchers could be used by Law enforcement, Government agencies, Criminals, Political parties and Security experts. It’s hard to detect IMSI catchers as there disguised as mobile phone towers.