Learn Kali Linux The Easy Way Getting Started With Kali Linux
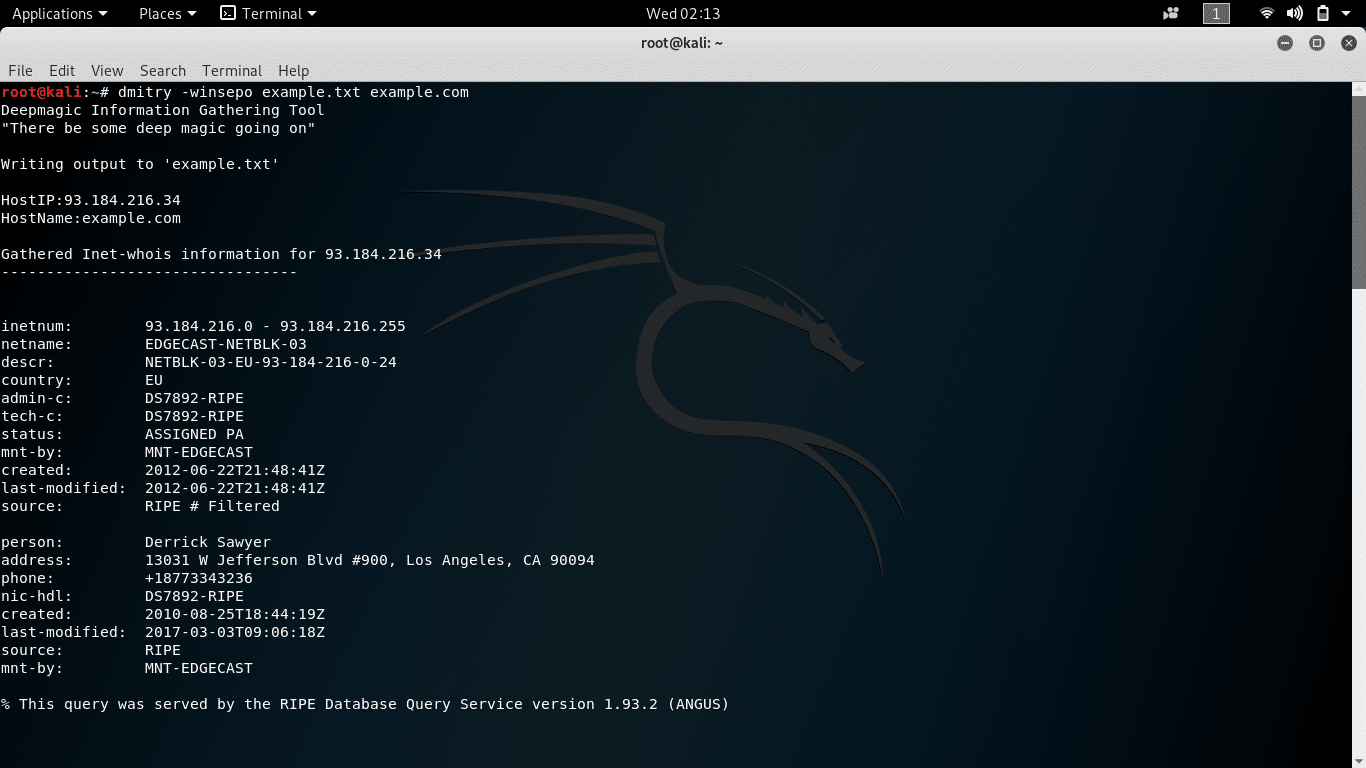
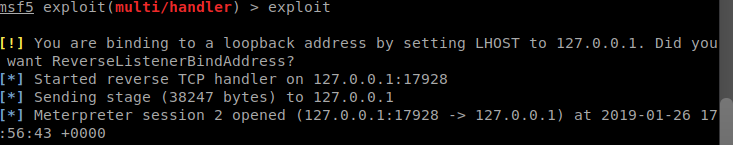
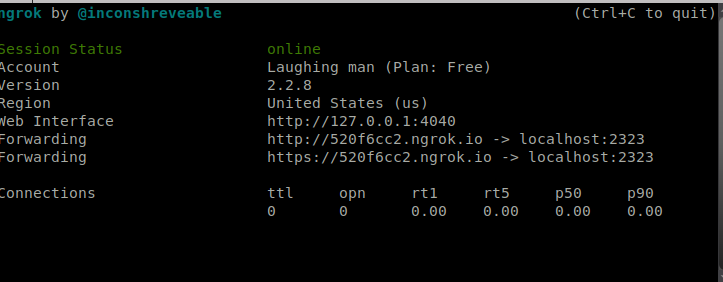
Learn Kali Linux The Easy Way Getting Started With Kali Linux Learn Kali Linux: Welcome to HackingVision, you have installed Kali Linux and you’re wondering how to use some of the popular and powerful tools included in the Kali Linux Operating System. Don’t worry we have put together some tips and tutorials to help you … Read more