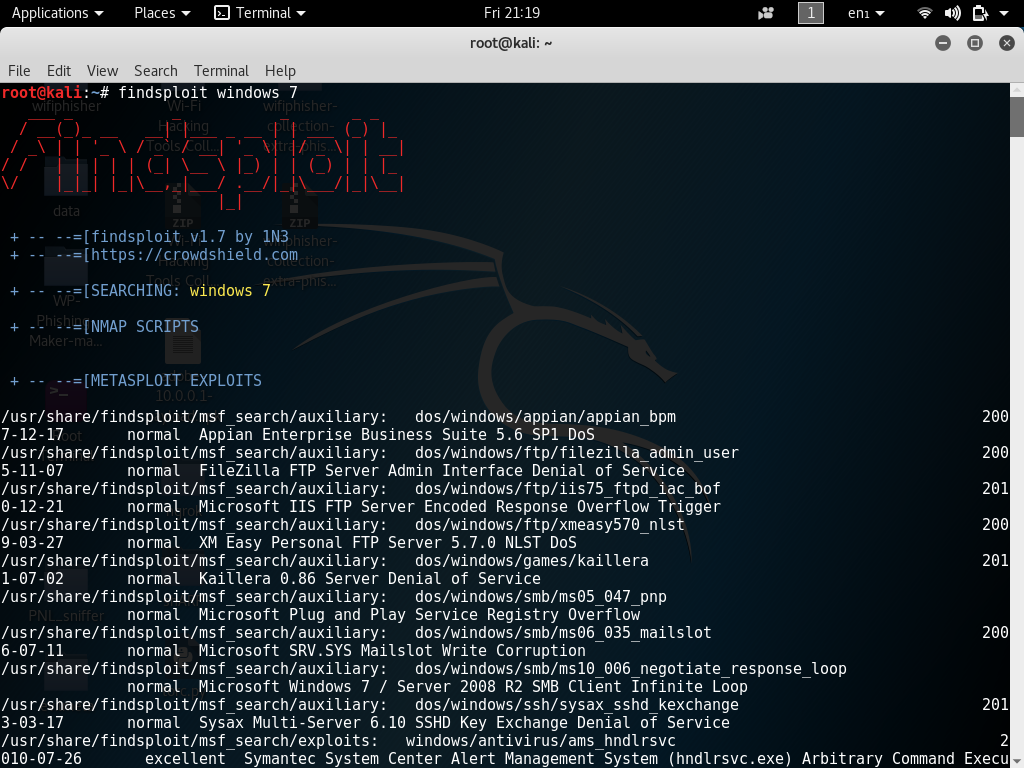
Slaughterbots is a short video by Stop Autonomous Wepons that shows the threats of weponizing AI and drone technology. This video shows threats from technology we already have. These drones have precision mapping technology that allows them to map a room in real time and teach themselves to perform aerial maneuvers that human controllers cannot possibly perform.
WATCH: Slaughterbots – Autonomous Weapons
If this isn’t what you want, please take action at http://autonomousweapons.org/