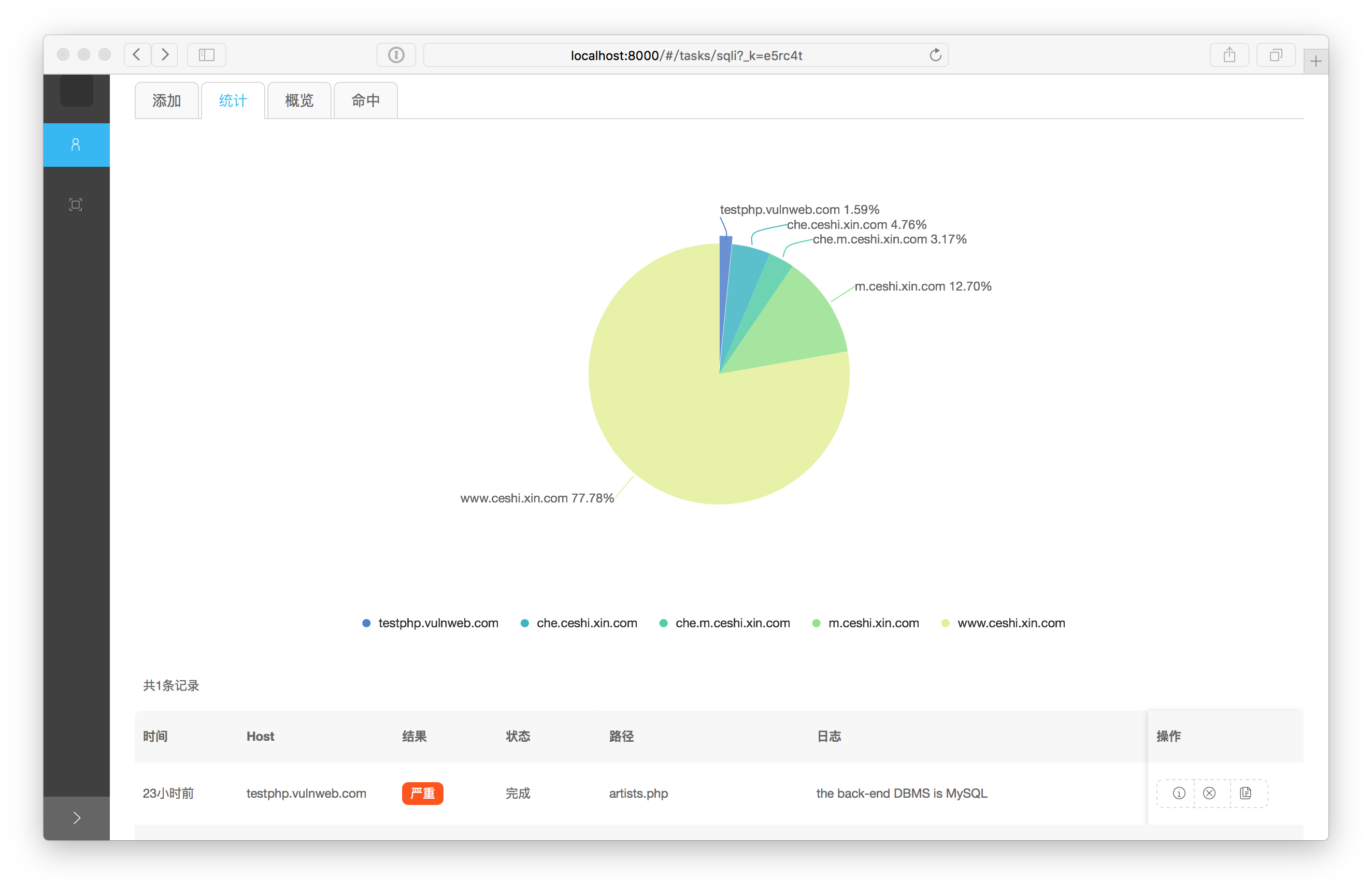
SQLiScanner – Automatic SQL injection with Charles and SQLMap API
Automatic SQL injection with Charles and sqlmap api Download SQLiScanner (Credits 0xbug) – http://0r1.me/SQLiScanner/ Github: https://github.com/0xbug/SQLiScanner Installation Preferably, you can download SQLiScanner by cloning the Git repository: git clone https://github.com/0xbug/SQLiScanner.git –depth 1 You can download sqlmap by cloning the Git repository: git clone https://github.com/sqlmapproject/sqlmap.git –depth 1 SQLiScanner works with Python version 3.x on Linux and … Read more