Smith – Client/Server Style Agent For Testing Network Connectivity
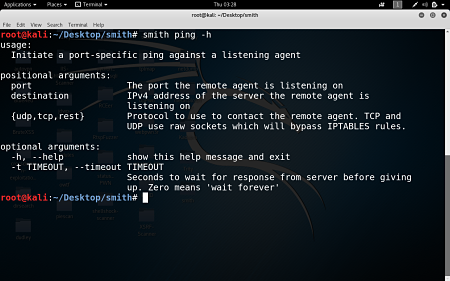
smith Credits: jidir (Leave him a star on Github) Download Smith A client/server style agent meant for testing connectivity to and from a machine on a network. Installation python setup.py install or pip install . should install smith. Note: If you want to use the tcp/udp protocol options, you’ll need to install scapy and it’s … Read more