For fun and profit, I’ve been participating in some CTF Capture the Flag challenges recently. I came in third place and am quite pleased with my performance. Allow me to take you through some of the CTF challenges in which I have participated.

Hogwarts Recruitment for Cyber Staff
This was a Harry Potter-themed capture-the-flag game that incorporated several online security tasks. CloudSEK hosted the event as part of the EWYL-2022 program.
Objective: Interns are needed at CloudSEK. Lisa from Hogwarts, one of the Cloudsters, designed a CTF platform for hiring. As a result, since this is the initial step in the employment process, we will conduct a pen-testing evaluation on the “Hogwarts Recruitment for Cyber Staff” CTF.
IP Address of Target: http://13.253.95.179/
Let’s get started. We can look at the index page of the website hosted on the target IP address by entering the target IP address into a browser. We can see that there is a button on the website that, when clicked, takes us to a gateway page.

We’ll be greeted with a page requesting us to log in once we’ve been sent to the appropriate gateway.

We’ll do some enumeration because we need to offer user credentials that we don’t have.
Interesting! On the server, there is a file called ‘wizardry.txt’. After reading the message to Lisa on the Portal to the Magical Realm, Look at the content of ‘wizardry.txt,’ I get the impression Lisa is trying to communicate. Examine the last paragraph of Lisa’s message on the Gateway to the Magical Realm. I get the impression Lisa is trying to express something along the lines of “look at the content of wizardry.”
I was right. Lisa is attempting to elicit a response from us! We can see a large encoded string in the ‘wizardry.txt’ file. We can know that the text is encoded in base64 just by looking at it.

We have the decoded string, but please wait a moment. This text appears to be encoded as well.

What kind of hashing algorithm are you using? Well, I found JSFuck after doing some research on Google using keywords like “esoteric encoding with brackets.” So let’s give the JSFuck decoder a go.

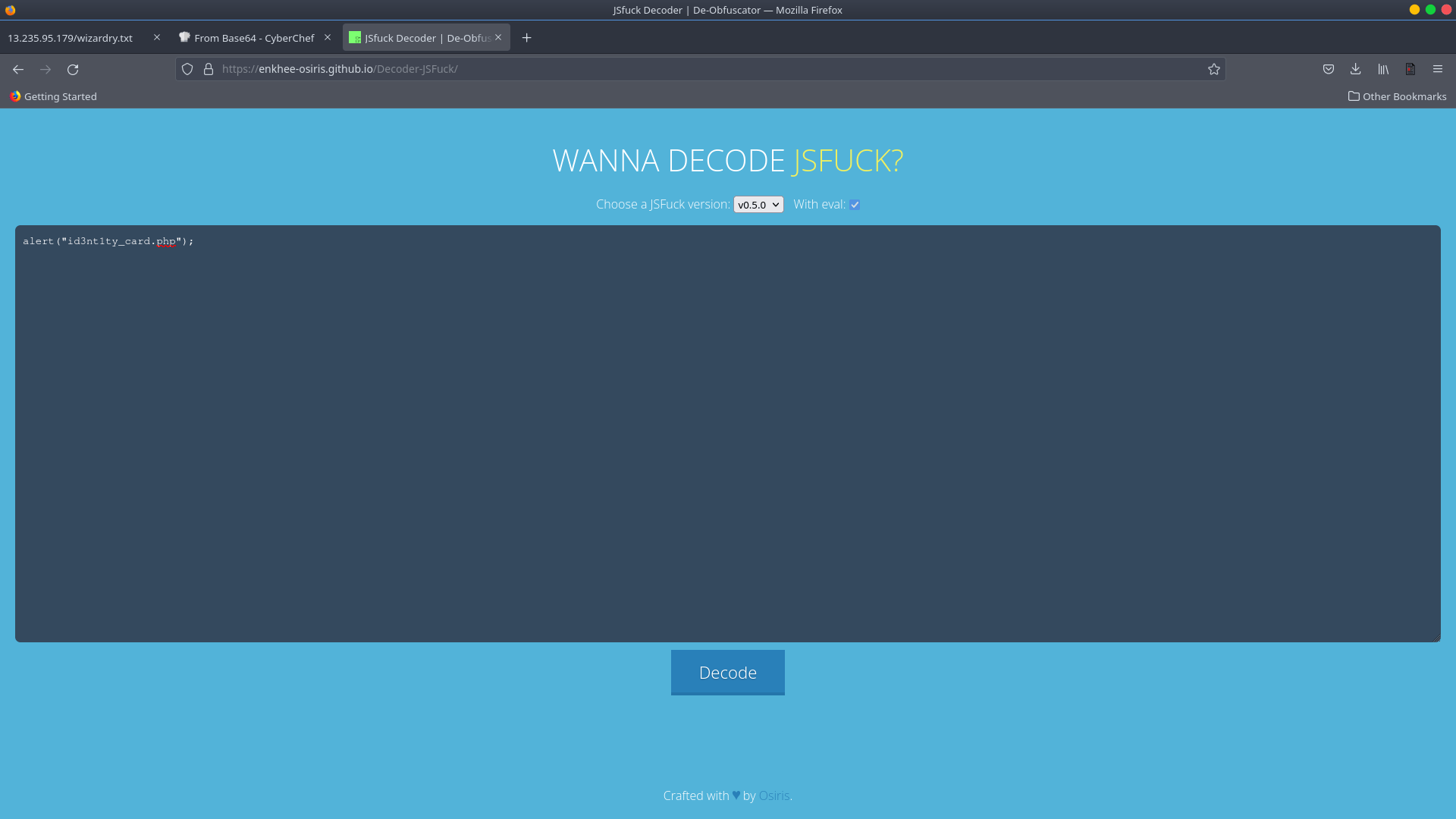
With the JSFuck decoder, we were able to correctly decode the text.
The decoded string is
alert("id3nt1ty_card.php");
Identity Card Challenge
There were numerous challenges in the CTF. The Identity Card Task was the following challenge, and after examining and closely scrutinising the photos in id3nt1ty card.php, we can see how “IDentity CArd” was written.
I discovered this after some trial and error…
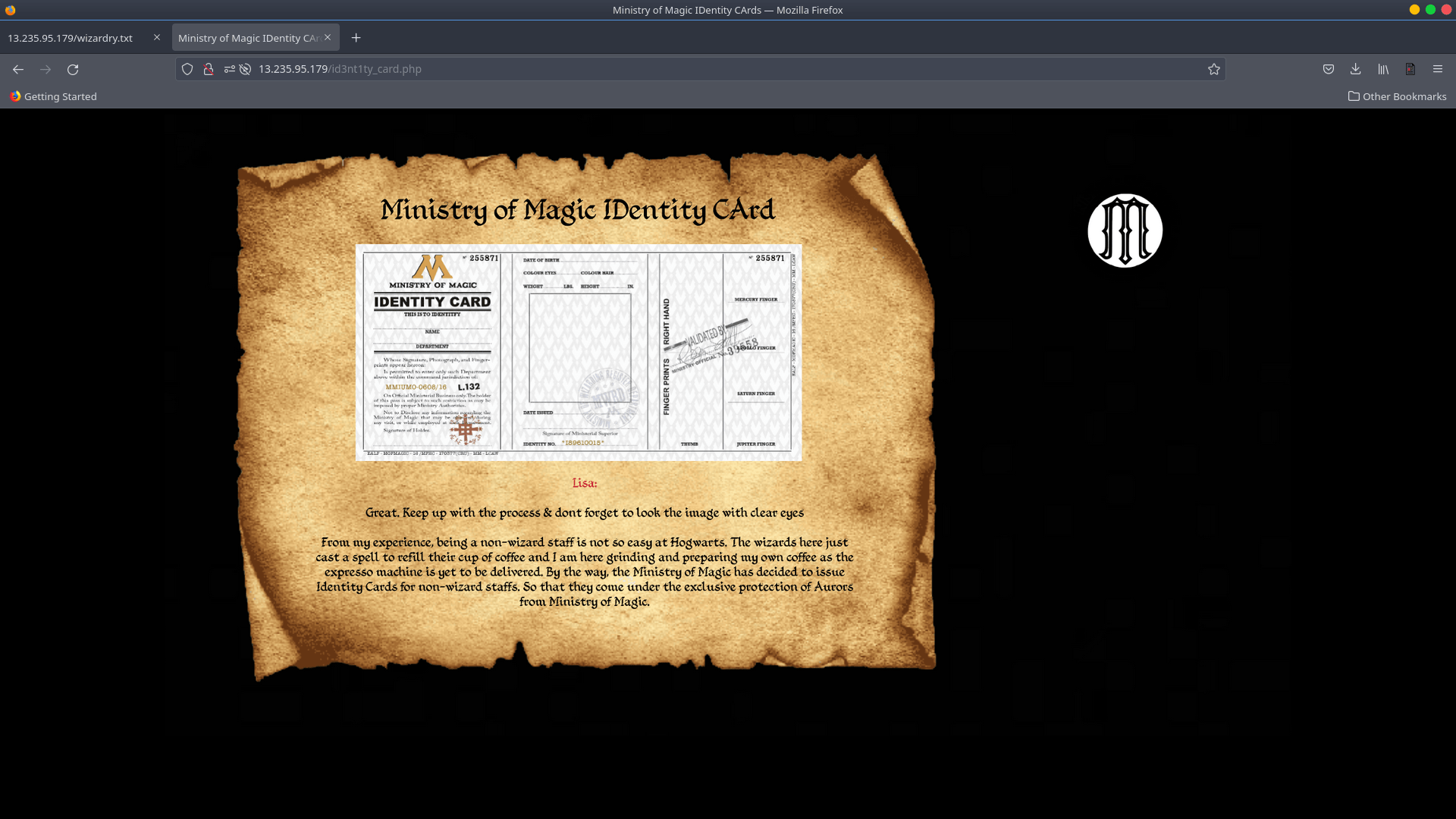

The photos depict a web page with information on IDentity CArd’s. PHP is used to create the page.
We can find some information by knowing the ID and including it in our query.
We discovered something intriguing after examining id=4. A strange term.
We get this notice if we use the number 212 in our id parameter on the identity card page. We can see the X and Y values there. Because the X value is encoded in base64, we can easily decode it.


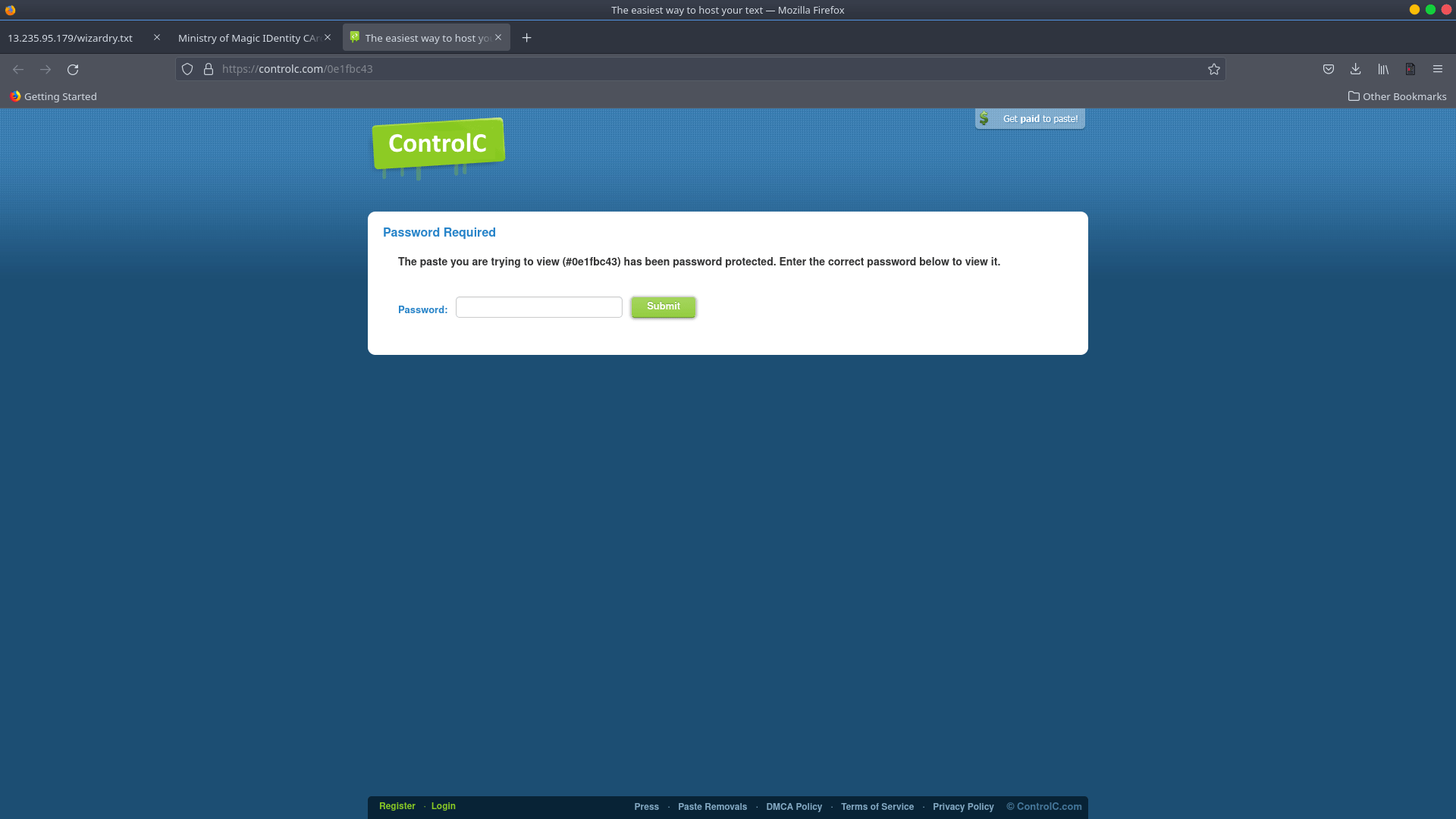
Let’s take a look at the value Y, which leads to a Pastebin. Because we don’t know our login credentials, ControlC prompts us to input them. We may utilise enumeration techniques instead. We can obtain some important information by looking at the page source of the preceding page. We discovered a png file with information on a phpcard.

If we can figure out how PHP code works, we’ll be in good shape. The password for the password-protected Pastebin that we discovered before may be retrieved.
$_REQUEST['passphrase']
The password is stored here. The password is validated by the code. We can see that when we make a request, it calls a function. strstr() is a function that returns a string.
“carbonblack” appears in the password string. Everything has been going well thus far. Let’s have a look at some more number circumstances.

When a string with numeric information is evaluated, the starting value of the number is checked. The comparison operation is then double-checked with the second integer operand.

A string is compared to numbers. It makes no difference what the number is! When comparing values, only the first value matters. I started with one and then compared them. The outcome is determined by the value entered.

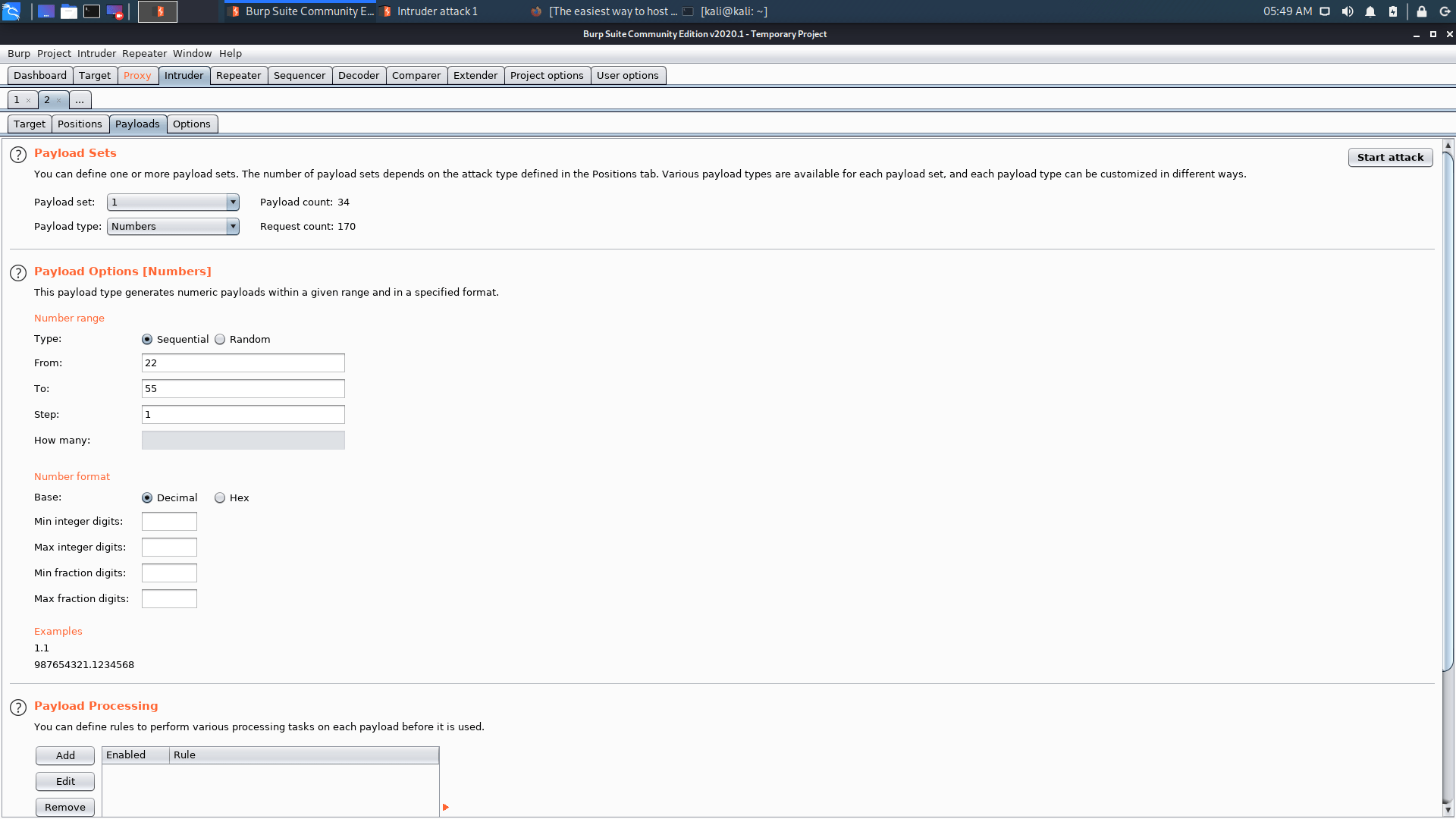
Brute force is not permitted on the CTF Server, although it is permitted elsewhere. I considered brute-forcing the ControlC Pastebin password with numbers ranging from 22 to 55. As a result, in burp, I set
$no$carbonblack
We use brute force to achieve our goals.
$no$ with 22 to 55 number.

There you have it, the length difference! We also discovered ControlC Pastebin’s password. Let’s login.


Look, we also discovered the value of Y.
"W0rk_iS_FuN"

The final password is obtained by combining X and Y.

We may now use the password we discovered to log into the gateway. Remember that on the identification card page, we used id=4 to find the username.
Chocolate Frog Collection Card / Steganography Challenge
Once we’ve completed our work, we’ll be able to download the photo.

Using the string command, we checked the strings and discovered something interesting. That unicode key 7 belongs to Krasy8.

Encryption – Decryption
We discovered a repo that would decode the Krasy8 unicode key 7 after a quick Google search.


We obtained our decrypt text, which is the level 1 flag, after executing that Java app. This is the flag.
"Level_1_Cl0uD_sEk_WiNFlAg"

SSTI Vulnerability
If we look closely at the third graphic in section 2.4, we can see that it implies that the level 2 challenge begins at port number 5000.

If we look closely at the third graphic in section 2.4, we can see that it implies that the level 2 challenge begins at port number 5000. After you’ve finished reading the entire text. We can see that there’s something with?search=, so I just add that field to the url and give it a value like “Hey,” as shown below.
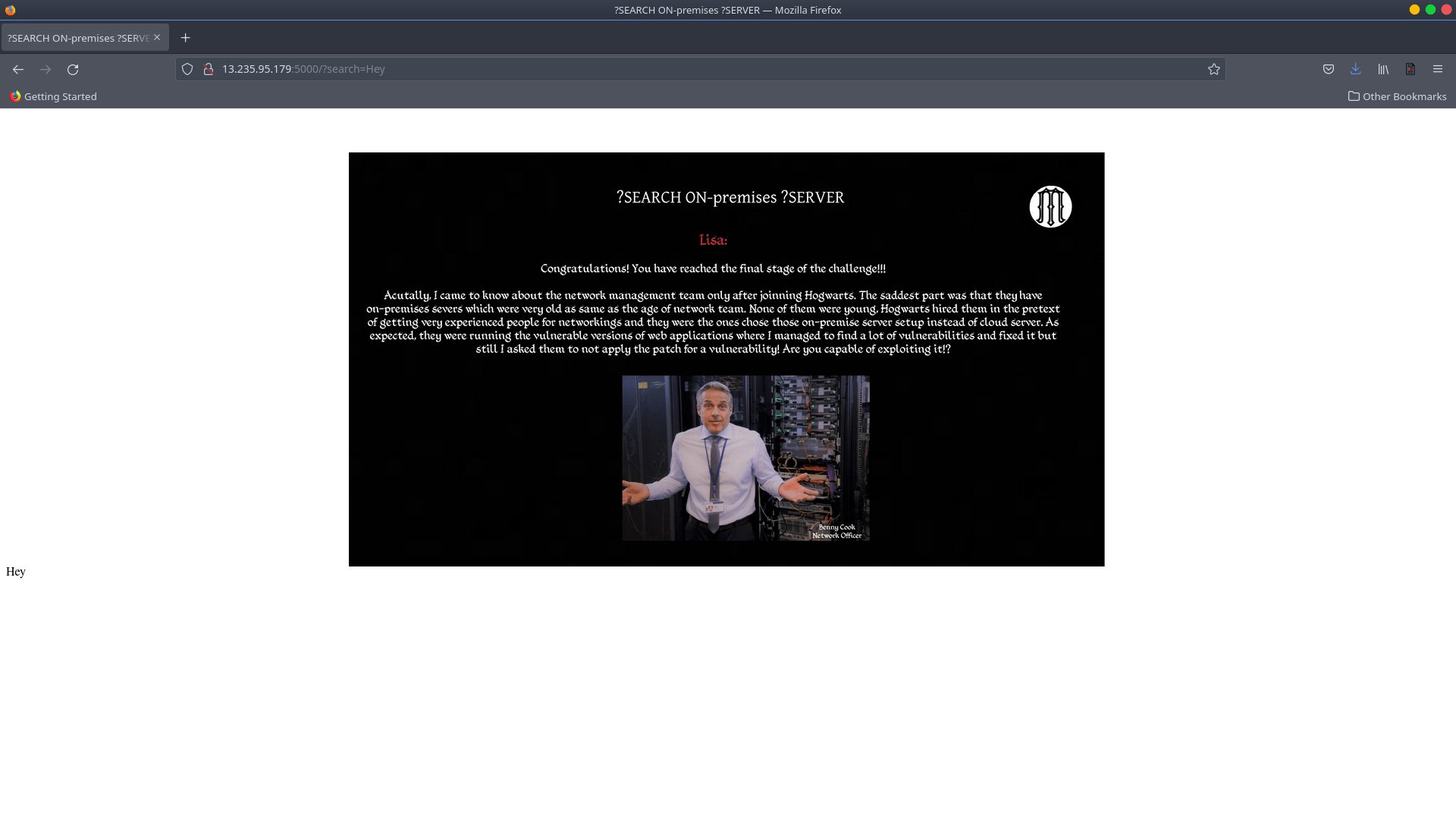
When I noticed that the text was reflecting, I immediately thought of the SSTI attack and tested the most famous payload, {{7*7}}, which yielded the predicted result of 49.

I went to the payload section of the repo to look for payloads relevant to SSTI Jinja2.


We discovered something intriguing in the secret key field when we attempted the config payload. The route /adieu is mentioned.

Passive Recon
We get the screenshot below after accessing /adieu.
After looking at the source code. A secret text and GitHub repo link can be found. It appears that it is instructing us to do passive recon.

When we check at the GitHub repository, we notice the Error Code 404. Maybe the repo is secret, or maybe it isn’t there at all.

I looked into that GitHub account some further and discovered Git-Tutorial Repo.

In the “Hogwarts The Hacker” file of the Git-Tutorial Repo, I discovered a GitHub access token.

We decode the token since it is encoded in base64.

We decode the token since it is encoded in base64. So, because we have the token for that GitHub account, we can access the private repos as well, so I used that token to download the “cloudSEK-CTF” repo, and it worked. After performing some additional exploration with the grep tool to locate a flag on that repo, I discovered our last flag, which is
"CTF{Congratulations_Level02_Completed}"


