WanaCry Ransomware still a threat two years on – HackingVision
Widely infamous WanaCry Ransomware is still a threat two years on.
WanaCry Ransomware and the EternalBlue exploit are still causing problems two years on.
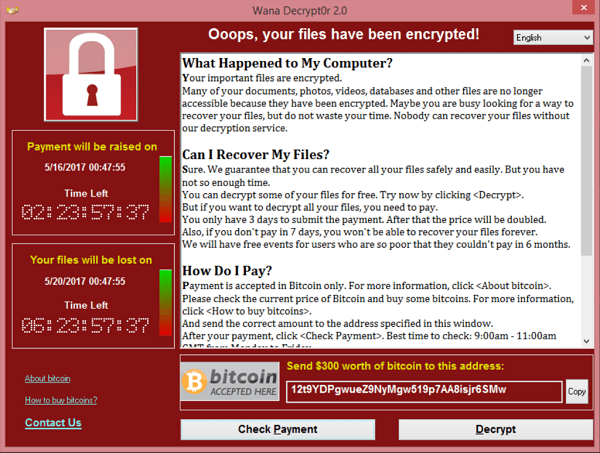
In May of 2017 Cryptoworm Ransomeware WanaCry started to target systems worldwide, the Ransomeware was targeting computers and devices that run older variants of Microsoft Windows operating system at a massive scale. WanaCry worked by propagating an exploit leaked by National Security Agency called EternalBlue.
WanaCry encrypted user’s data and demand a ransom in the form of cryptocurrency Bitcoin (BTC) in value of $300 – $600 in order for the infected user to obtain the decryption keys for there system that are needed to decrypt data encrypted by WanaCry. The infamous Ransomware infected over 200,000 users and around 300,000 devices from 150 different countries around the world. Including the NHS, for those who are not familiar with the NHS, this is the National Health Service in the UK. The US NSA National Security Agency had discovered the ExternalBlue vulnerability but instead of disclosing the exploit to Microsoft they used the exploit to create an exploit for its own security work, EternalBlue targets Windows’ Server Message Block (SMB) protocol on 14th March 2017 Microsoft issued a security bulletin MS17-010 to address the flaw. Microsoft announced that patches for all versions of Windows affected had been released to the public.
Microsoft’s patch was only pushed for supported versions of Windows. There are many outdated and unsupported versions of Windows that are still vulnerable to EternalBlue exploit. The versions of Windows that were patched are
- Windows Vista
- Windows 7
- Windows 8.1
- Windows 10
- Windows Server 2008
- Windows Server 2008 R2
- Windows Server 2012,
- Windows Server 2016.
The External Blue exploit was first leaked by a group of hackers called The Shadow Brokers prior to the WanaCry cyber attack. WanaCry Crypto-worm Ransomware was spread through organizations that did not Install recommend patch for the EternalBlue exploit released by Windows. Many of the organizations that were hit by the WanaCry Ransomware campaign were using systems that operating were at their end-of-life and were no longer receiving updates or support from Microsoft.
WanaCry took the opportunity to install backdoors rootkits onto the infected systems. The cyberattack lasted 4 days before being completely patched by a security researcher called Markus Hutchins from the UK who found a killswitch in WanaCry by finding the hidden killswitch in WanaCry Markus Hutchins prevented the Ransomware spreading to more systems.
WannaCry Ransomware Infection Heat Map
Who was to blame?
Security experts believed from preliminary evaluation of the worm that the attack originated from North Korea or agencies working for the country.
In December 2017, the United States, the United Kingdom, and Australia formally asserted that North Korea was behind the attack. Suspects included the Hacking Group Lazarus Group.
https://en.m.wikipedia.org/wiki/WannaCry_ransomware_attack
In August 2018 a new variant of WanaCry Ransomware targeted Taiwan Semiconductor Manufacturing Company (TSMC) this caused the company to temporarily shut down its operations at several of its chip fabrication facilities. The virus spread to 10,000 machines within TSMC’s advanced chip fabrication facilities around the world.
later in June, hundreds of computer users reported an email that came from someone or multiple malicious spammers claiming to be the creators of WannaCry Ransomware. The email that was sent to the users threatened to destroy the victims’ data unless they sent 0.1 BTC to the Bitcoin address belonging to the hackers.
“Two years after the WannaCry ransomware attack, PUBLIC’s senior technologist David Williams analyses NHS’s cyber-defense strategy & the lessons to take from government IT, in general.
Avast identified the WannaCry ransomware attack as “one of the broadest and most damaging cyberattacks in history”. It affected more than 230,000 computers worldwide and, while it did not target the NHS or any government systems specifically, its impact on day-to-day healthcare operations in the UK was enormous. A targeted hack, like the one that compromised the healthcare records of 1.5 million patients in Singapore, could totally destroy the public’s trust in the NHS to safeguard its health records.”
In a comprehensive review published early 2018, the NHS determined that it had, in fact, made all trusts aware of the Microsoft vulnerability that the ransomware exploited on April 25th via its CareCERT bulletin, only 24 hours after being informed of it. By the time the attack started 3 weeks later, however, none of the 80 trusts which were affected had applied the patch to their Windows 7 systems, and 18% of devices were still running unsupported Windows XP (in spite of two programs, launched in 2010 and 2014, to help trusts to migrate away from the OS).
Security firm Malwarebytes marks WanaCrys two year anniversary by publishing a study analyzing how many machines have been infected by WanaCry Ransomware since 2017. While we have seen a massive decrease in cyber-attacks of WanaCry variation of ransomware since Security researcher Markus Hutchins found kill switch for WanaCry ransomware in May 2017.
WanaCry ransomware was detected on 4.8 million systems around the world that have been identified by Malware Bytes since May 2017.
ASAM Kujawa Director of Malwarebytes says that there still remain many unpatched systems connected to the internet that are still vulnerable to WannaCry ransomware.
Computer systems around Eastern Europe and Asia remain unpatched.
Countries with the most WannaCry detections
Malwarebytes says the figures, are
- India (727,883)
- Indonesia (561,381)
- USA (430,643)
- Russia (356,146)
- Malaysia (335,814)
With the sheer amount of computer systems that are still vulnerable to External Blue, External Romance exploits. Techniques used by these exploits are helping new trojans infect businesses and organizations with new variations of malware. Cybercriminals are still using EternalBlue exploits to their advantage by creating undetectable and more advanced variations of malware that can easily take an undetectable state. Expect to see a lot more malware with similar traits in the future. Emotet and Trickbot malware are two popular examples. Trickbot and Emotet malware have demonstrated just how successful some of these malware campaigns can be.
Shodan EternalBlue Report
https://www.shodan.io/report/S8dhzrSn
Due to the killswitch feature that was found inside WanaCry made this ransomware unreliable we are quite certain there should not be many attempts if not any in the next couple of years to spread WanaCry Ransomware.
If you would like to read More about WanaCry Ransomware and the EternalBlue exploit you can find a lot of good information on Wikipedia.
https://en.wikipedia.org/wiki/WannaCry_ransomware_attack
https://en.wikipedia.org/wiki/EternalBlue
