How Thieves Can Target High-End Devices Using Wifi Signals
Your wireless devices could be leaking information about them selfs to hackers and criminals or anyone with a smartphone.
Wifi signals
Disclaimer
HackingVision does not condone the illegal use of this software nor does it promote the illegal use of this software mentioned in this article. The content is provided only as a convenience to the educational and security community.
It seems thieves can be anywhere looking for the opportunity to steal your goods a lot of thieves will target high-end Smart Phones and wireless devices.
Many users have asked me why not just get a smartphone blocked if it’s stolen ?. Quite often they are blocked, however, a loophole allows thieves to ship stolen phones to regions where the devices would be fully functional and not compliant to the restriction placed by the mobile service provider.
Unfortunately, to catch thieves in this digital era we must play a bit of Cat & Mouse and use the very methods they use against them. Let’s assume we are in an area that has a high theft rate, 90% of thefts in the area were all related to wireless technologies, high-end Smartphones & Smart TVs. One could then create a Wireless Mapping of all clients and access points in range finding there SSIDs and other sensitive information such as PNL & PNL lists (Preferred Network List).
Information preferred network lists allow wireless devices to send PNL requests to check if a network is available. We could then start looking for stolen devices probing for SSID to connect back, this, in turn, allows law enforcement to track down stolen devices that are still looking for a Wireless Signal to connect with. The very same methods could also allow thieves to target high-end devices Such as Smart TVs, Phones, Gaming Consoles, and many other expensive Wireless Devices.
Wireless Wardriving
What is Wardriving? Wardriving is a technique used to detect and map Wireless networks in a moving vehicle by using a laptop or smartphone.
Wikipedia – “Wardriving is the act of searching for Wi-Fi wireless networks by a person in a moving vehicle, using a laptop or smartphone. Software for wardriving is freely available on the Internet.”
Warbiking or Warcycling is similar to Wardriving but is done from a moving bicycle or motorcycle. This practice is sometimes facilitated by mounting a Wi-Fi enabled device on the vehicle. Warwalking, or Warjogging, is similar to Wardriving but is done on foot rather than from a moving vehicle.
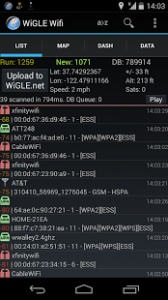
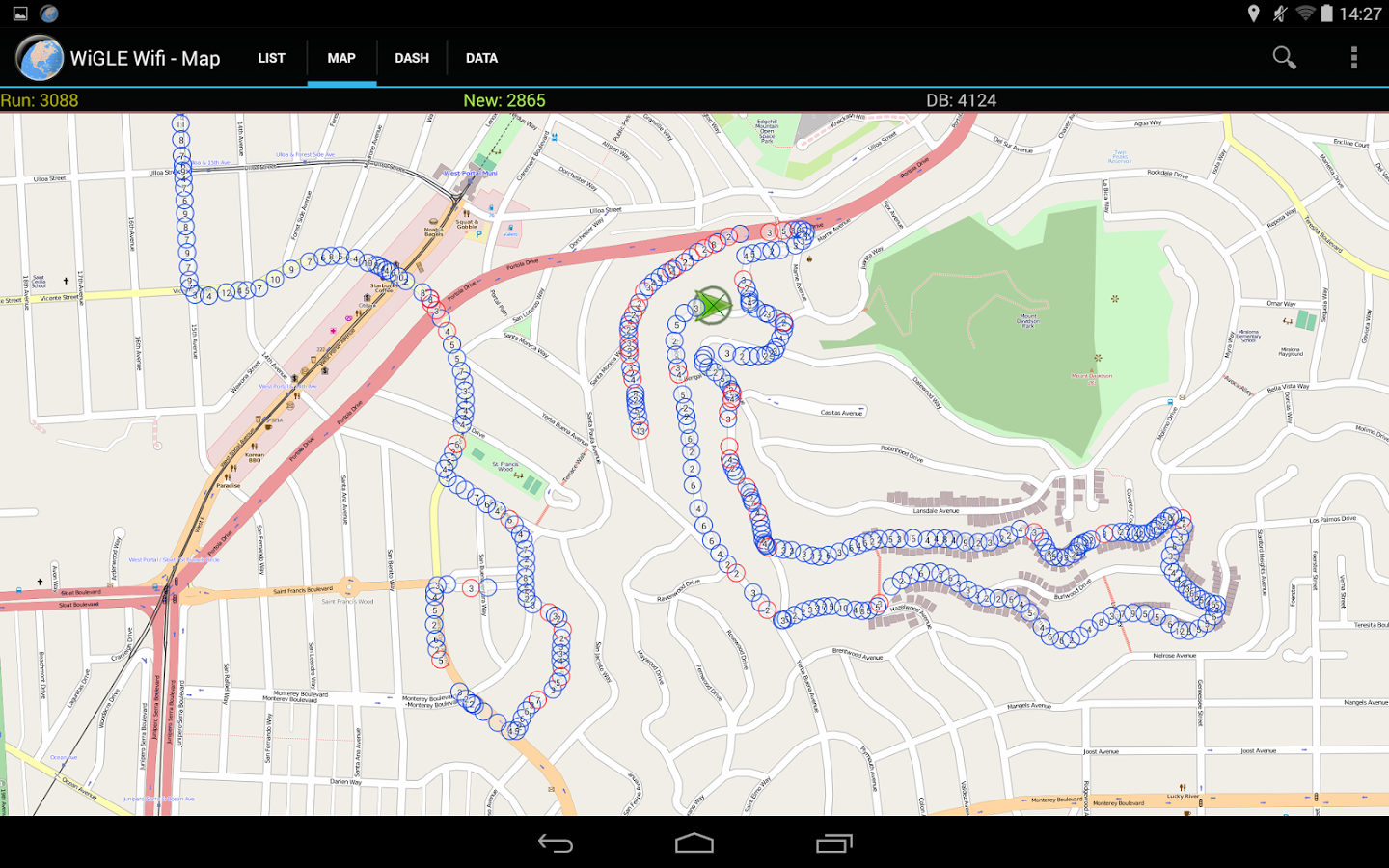
So, let’s begin, today we will be looking at how thieves & cybercriminals can target high-end devices using WiFi signals. While searching for Wireless Testing Tools on Google Play Store, I came across an App called “Wiggle Wi-Fi Wardriving,” which is used to map wireless devices within a certain radius and log them to an online database. Details then would be uploaded to a database online by standard, the application does scan for probes and various clients so I turned the option from the settings.
I was ready to create a full map of my village. Why did I want to map my full village? I have done a study on WPS pixie dust attacks a while back, I noticed many D-Link router vulnerable to Pixie Dust WPS after the company in question got a lot of exposure, they then reclaimed a lot of routers but not all of them. So I continued my case study, a couple of years had passed since this attack was causing havoc. I wanted to see how many people out of 1000 routers belonging to the brand D-Link distributed by TalkTalk are still using old hardware.
You can read more on our findings on D-Link TalkTalk routers here this will help you understand why wireless wardriving can also be useful in some cases.
So we then went to a fairly popular area to conduct our test we scanned 1000 Access Points excluding clients and out of 1000, 250 of which were still using older vulnerable D-Link routers and 25 percent of clients could still be exposed to these threats. Anyways it got me thinking I will do a second mapping, this time including Wi-Fi clients.
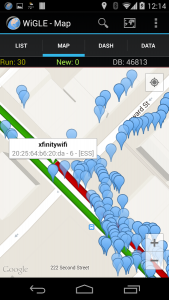
Wiggle uses Wi-Fi in combination with GPS and a Google Mapping system to view the location of various Wireless Access Points and Wireless Clients, it can also pinpoint the distance of the device by calculating the Power of the target Wireless Devices in correspondence with the Attackers GPS location.
I began to walk around noticing various Wireless Clients showing up and being mapped out to an interactive mapping system similar to the type of interactive maps you might see on a SatNav or GPS application, it then, in turn, allowed me to walk around mapping Wireless Devices to the database, I started noticing hi-end devices such as Samsung Galaxy S8, Sony Playstation PS4, Xbox One and various other High-End devices including smart TV’s and Gaming Consoles.
Not only could I see the Geo-location of the devices, but I could also use a super accurate prediction of whereabouts of the devices, in question this then let me predict what rooms or whereabouts in the houses the device were hidden or kept. I then thought, let’s assume this Application was to fall into the wrong hands it could allow thieves to potentially predict about house’s best and most expensive goods.
This article is not here to teach you how to steal it’s here as a convenience to the educational and security community if you are using this article for illegal purpose please leave now ! This article is here to demonstrate how an attacker would target wireless devices using Wardriving software.
There are many Wireless Wardriving Applications for both Android and Desktop. In this article, I will list an example of a popular Wi-Fi Wardriving application for Android.
Wiggle Wi-Fi Wardriving
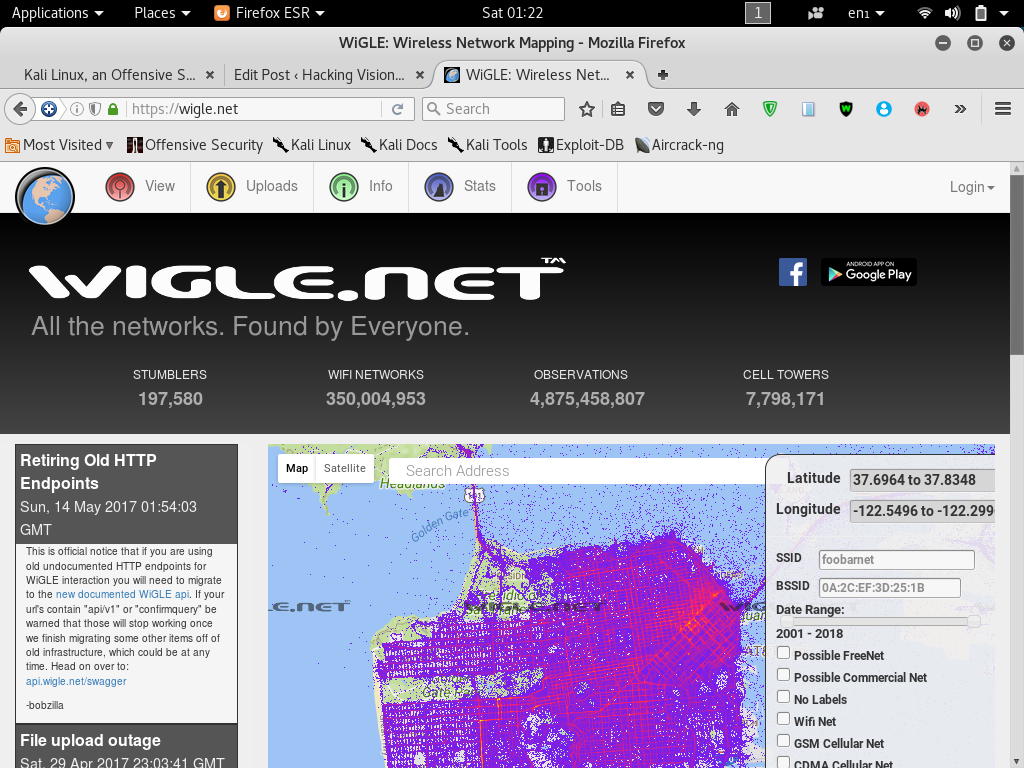
Wiggle is an open-source wardriving app to netstumble, display and map found wireless networks and cell towers anywhere in the world, easily uploading to the http://wigle.net database. WiGLE was started in 2001 and now has over 250 million wifi networks worldwide.
Conclusion & Prevention
- Turn Wireless Devices off when not in use.
- Secure wireless devices with a password
- Secure wireless devices with an Anti-Theft Prevention App such as FindMyiPhone or Prey for Android, Google Device Manager or similar service.
- If the router accepts AP isolation, Wireless isolation consider enabling it

