WhatsPwn 2.0 – Linux Tool to extract sensitive data and inject payloads into any Android devices.
Credits: José Luis Rodríguez Fragoso (jlrodriguezf)
here is a new version of the Linux tool WhatsPwn which features new payload options like Meterpreter injection or the ability to create hidden or visible payloads and inject them into any android device. It is still in beta stage so there may be some bugs and some features may not work properly but updates are constantly rolling, so expect updates very soon.
You can find the complete changelog here.
This is a brief tutorial on how to use this tool, which just makes the process of extracting sensitive data like WhatsApp databases and photos, and injecting backdoor payloads a lot easier.
INSTALLATION
The first thing you need to do is clone the repository
git clone https://github.com/jlrodriguezf/WhatsPwn.git
REQUIREMENTS
By default, if the program finds that you’re missing dependency it will install it automatically. But if you’re curious these are the dependencies;
- Metasploit-Framework: If you are using Kali Linux 2.0 and for any mysterious reason you are missing this framework the program will install it automatically. Otherwise, you will have to install it manually. You can follow this, or this, or this, or any other guide for the installation and configuration.
- SSH & SSHPass
- Ruby: For injection as bash was not made for parsing XML files.
- Apktool
- Java 7: This is just for apktool to work.
Once you have done that we can proceed.
CONFIGURATION
There are two files that you might want to edit first, the config file and the server file.
MAIN CONFIGURATION
The config file is where you put all the main variables corresponding to your system. This is how the file looks like:
##############################################################################
# PAYLOAD OPTIONS #
##############################################################################
PAYLOAD=""
PAYLOAD_NAME=""
PAYLOAD_PORT=""
PAYLOAD_IP=""
LEGITIMATE_APK=""
##############################################################################
# MAIN OPTIONS #
##############################################################################
PATHEXT="~/"
BACKUPZIPNAME="filesystem_linux"
USER="--user 0"
AUTOMODE=1
Here is the list of all the configuration variables:
- PAYLOAD: It specifies the payload to use. If you already have your own you can put it in here with the full path and ending with .apk.
- PAYLOAD_NAME: This is the name of the output payload name without.apk. When you want to generate multiples payloads you might want to set the default payload name so that the process became more efficient as the program would not ask you for the name every time you want to generate one.
- PAYLOAD_PORT: The port to use for payload reverse connections. You may want to specify the default for the same reason as the above.
- PAYLOAD_IP: This is the IP the payload will connect back to. This is your external or internal IP or even your dynamic DNS address.
- LEGITIMATE_IP: This is the path of the legitimate app the program will inject Meterpreter to with full path. This is just for injection.
- PATHEXT: This is the path where all the extracted data is going to be. By default, this is the root directory.
- BACKUPZIPNAME: This is the name of the .zip file containing all the extracted data. By default this is filesystem_linux.
- USER: This is how the payload’s service will launch. You don’t have to worry about this as this is just for compatibility for some android devices.
- AUTOMODE: This boolean tells the program to ask for every variable that is missing in the FULL ATTACK at the beginning so once it has started you don’t have to worry about typing names or paths.
SERVER CONFIGURATION
If you have set up a server where you want to be all your extracted files you can place your configuration in the server file. This is how the server file looks like:
SERV
USRSERV
OUTPUTDIRSERV
This is very easy you just need to change the variables to suit your server configuration.
- SERV: This is the IP to connect, this can be an external or dynamic DNS name.
- USRSERV: This is the username of the server, i.e, root.
- OUTPUTDIRSERV: The path to put the extracted de data.
Just to clarify things, the program will try to connect to USRSERV@SERV/OUTPUTDIRSERV.
HOW TO USE IT
As this is a CLI Framework there are no arguments to parse, that means that you can just run it by.
./whatspwn
Or from any directory. For example, if you cloned the repository to ~/Downloads/, you can run it as;
~/Downloads/WhatsPwn/whatspwn
This will take you to the license agreement prompt where you have some options, you can type y to agree and continue.
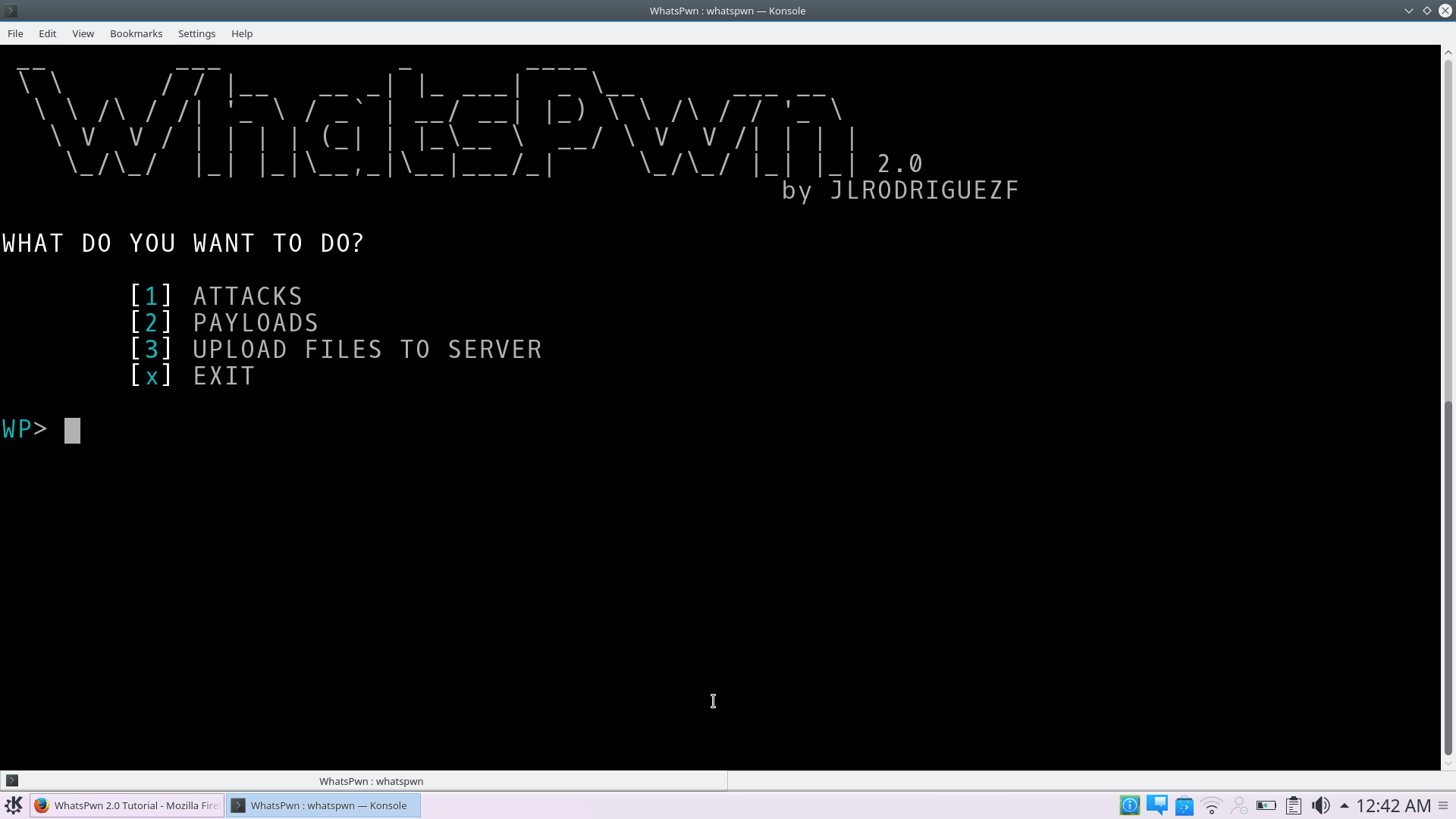
Next, it will take you to the main interface where all the fun begins.
This is how it looks:
ATTACKS
When entering attacks menu you will need to connect your device via USB cable, so you will have to enable ADB Debugging on your Android device, to do so you can follow these steps;
- Go to Settings > About > Software
- Tap 7 times on Build Number to enable Developer Options
- Go back to Settings
- Tap on Developer Settings
- Turn on USB Debugging
After ADB Debugging has been enabled and you have connected your device you will be taken to the attack’s main menu. Here you can choose;
- Full Attack:
- Get the device main info like model, version, manufacturer, etc.
- Install the backdoor payload you have specified in the config file.
- Extract the WhatsApp Database, decrypt it and save it. To do this, WhatsApp on the device will suffer a temporary downgrade, but don’t worry, the program will restore the version that was installed and keep all the data. Only in case of error or incompatibility you will have to Emergency restore WhatsApp.
- Extract sensitive data
- WhatsApp images, sounds, etc.
- DCIM images.
- Telegram images.
- Shell: Launch a shell to the device.
- Emergency restores WhatsApp: This is only in case of error or incompatibility. This will restore downgraded WhatsApp to the last version, but sadly it won’t restore conversations or user data.
- Only extract sensitive data: This will skip the payload installation, WhatsApp Database extraction, and decryption. It will only extract photos and sensitive info.
- Install or relaunch payload: This will install the payload specified in the config file or created in the payloads menu, and start the service.
Note: If the connection was successful it will do all the processes wirelessly, otherwise, you will have to keep the phone connected.
PAYLOADS
Typing 2 in the main menu will take you to the payload’s main interface. Here you can choose;
- Injection: This will inject a Meterpreter code into a legitimate app.
- Create hidden payload: This option will create a hidden Meterpreter payload, in other words, this will not show up in the applications drawer on your device.
- Create visible payload: This is the opposite of the above.
UPLOAD
This option will try to upload all extracted files to the server specified in the server file.
Other tools you may like:
https://hackingvision.com/2017/07/16/hacking-android-smart-phone-using-ahmyth-android-rat/