#Hackers have found a way to download a malicious file when a hover action is performed over a #hyperlink. The interesting fact about this technique is that it did not rely on Macros, JavaScript or VBA for the execution method. This makes it unique as it does not uses normal exploitation methods as most of the Office Malware relies on users activating macros to download some executable payload which does most of the malicious operations.
This new variant of malware dubbed as “Zusy” has been found in the wild spreading as a PowerPoint file attached to spam emails with titles like “Purchase Order #130527” and “Confirmation” according to a Senior Security Researcher at SentinelOne Labs.
Here is How Zusy Malware Works
The malicious PowerPoint presentation file is delivered to potential victims as a file attachment with spam emails with titles like “RE: Purchase orders #819279” or “Fwd: Confirmation“. When the victim opens the PowerPoint presentation file which is in the PPSX file format, the powerpoint file opens in slideshow mode instead of the edit mode.
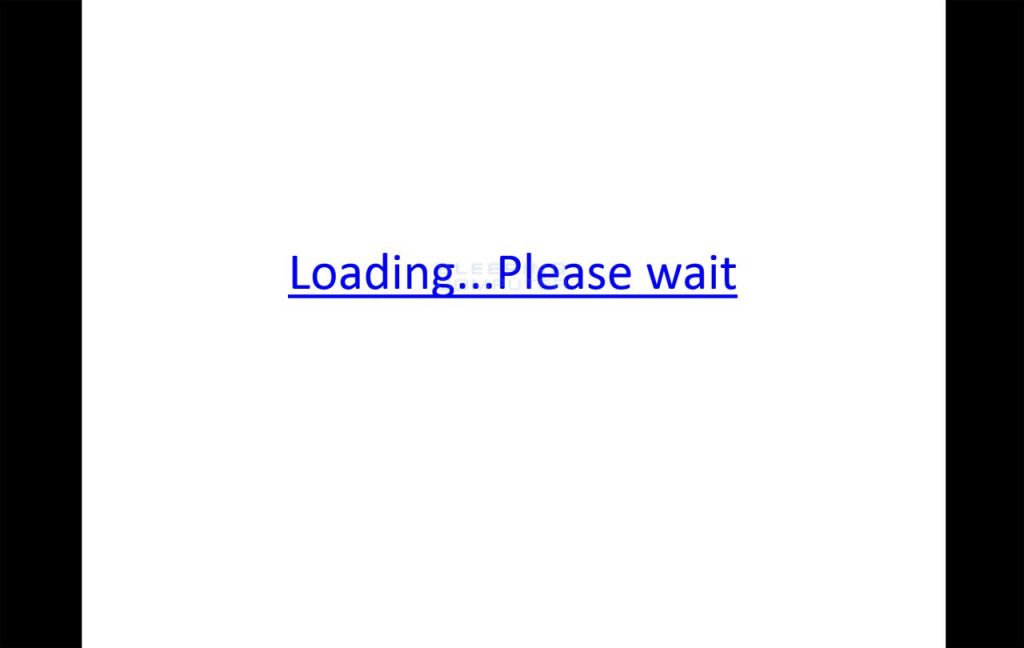
Then the victim is able to see only the hyperlinked text “Loading… Please wait“, and when he moves the cursor over the hyperlinked text the document will start executing PowerShell command that runs an external program and create a backdoor.
“When the user mouses over the hyperlinked text it results in Powerpoint executing PowerShell. This is accomplished by an element definition for a hover action. This hover action is set up to execute a program in PowerPoint once the user mouses over the text,” said security researcher Ruben Daniel Dodge in his report.
The presentation files look like this:
Here is How To Be Safe from This Malware
Usually, most of the Office malware relies on users activating macros to download some executable payload which does most of the malicious operation, but this malware was different from them.
Fortunately, Microsoft Office comes with a security feature called a protected view which is by default turned on and prevents PowerShell command from executing an external program automatically. However, this feature can be turned off which is not recommended by Microsoft and from the security perspective. Microsoft spokesperson addressing the malware says “Both Windows Defender and Office 365 Advanced Threat Protection also detect and remove the malware.” according to Bleeping Computer.
A user should always be suspicious of the emails received from non-familiar sources and keep a reputed and updated anti-virus program installed in your system.

