Up to 25 Percent of TalkTalk UK Customers Could Still Left With Vulnerable Routers
Around 25 Percent TalkTalk UK Customers Could Still Be Left Vulnerable Routers Back in late 2016 exploits were found in D-Link DSL-3680 routers provided by TalkTalk. This exploit known as in the Hacker World as PixieWPS exploit left many home owners and businesses open to cyber attacks. Attacks such as man and the middle attacks could be carried out on the routers quite easily. These type of attacks can be lethal to businesses or members of the public as lots of information can be leaked to the attacking computer. The way a MITM attacks work is by tricking the target clients on the network in to thinking the attacking computer is the router. The way hackers exploit this vulnerability is through a flaw called PixieWPS this exploit take little more then a couple of minutes using the correct software. Pixiewps is a tool used to brute force WPS pins offline, while exploiting the low or non-existing entropy of some wireless access points also known as the pixie dust attack, it was discovered by Dominique Bongard.
If you don’t know what WPS is it stands for WPA/WPA2 (Wi-Fi Protected Setup) is impelled by most manufactures to secure routers & other wireless devices. It tries to make connections between a router and wireless devices easier and faster by using a Push Button on the router rather then entering the routers pass phrase.
Often when brute forcing WPS keys using standardized methods it can be a challenge due to restrictions put in place by the vendor such as AP locking. After a certain amount incorrect Pin attempts the router would lock in order to prevent further brute forcing it can take a while to successfully crack a network and be delivered with the correct password. When an access point has AP locking (Access Point Locking). It can take between 2, 4 up to 10 + hours. For those who are less tech savvy heres a explanation of how the attack would usually work on any bog standard router.
There are 100,000,000 Possible Key Values although the ending digit of the key value is known as a checksum witch is calculated based on the last 7 digits lowering the process down to 10,000,000 possibilities. WPS breaks the Pins/Keys in half during this process the keys are then broken down to 10,000 values for the first half and 1,000 for the second half of the key-chain this totals 11,000 possible pins to try lowing the overall time of this process drastically however this is not the case with the D-Link router in question provided and branded by TalkTalk does not have AP locking in place what makes this router so scary is that the default factory pin for WPS. Unfortunately to the vendor this is the first WPS key Reaver and other offline WPS brute force tools often try on there first cracking attempt this mean thats the attack does not need to filter through all 11,000 possible WPS keys. Instead the attacker would be sent back the routers WPS and passprase on the first key attempt.
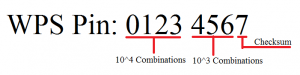
Read a little more about the vulnerability in 2016.
https://www.theregister.co.uk/2016/12/06/wifi_looting_router_hacking/
You can also see this attack in action back in 2016 TalkTalk provided us with one of these routers. After we noticed how insecure the network was we decided to cancel and not go ahead with the TalkTalk contact however ever TalkTalk did not want the router back even though it was a potential risk. Since we were supplied with this router there was countless vulnerability found including weak Admin Panel Passwords Username:admin Password:admin (This means that any user connected to network wireless or wired could potentiality change the password preform MITM attacks add the network to a botnet and even open up ports or change the DNS to display a fake page. This is one of the weakest routers that we have tested so far for example if an attacker was to open port 80 on the victim router the routers configuration page could be displayed remotely and the router could be remotely reset.
Read Disclaimer before you attempt to test your own router for vulnerabilities.
Image shows D-Link WPS brute force vulnerable router being cracked in 1 second.
The attack in question takes around 1 minute and will always get the password on the first attempt this is due the the way factory keys are stored within the routers as explained above using this factory key in all routers is a recipe for disaster. Could be one of the main reasons a lot of TalkTalk customers ended up being part of Mirai Botnet Worm ?.
TalkTalk replaced a lot of routers of angry customers who owned a TalkTalk D-Link DSL-3680 they would then be replaced with a more convenient and safer router from HAWAII TECHNOLOGY. However this can be a costly challenge replacing this much technology in such a short amount of time. We come to speculate that up to 25% of customers using the D-Link model router provided by TalkTalk could still be at risk and we don’t think that all were informed properly by the ISP in order to cut costs on replacements hardware. We encourage anyone with one of these routers to turn of WPS immediately.
So to back up our claims we done a little analytics of our own. We scanned 250 TalkTalk Routers within a 1 mile radius using a popular Wireless Analytics Application called Wiggle To carry out our study. We found that more then 25% of TalkTalk routers where still using TalkTalk D-Link DSL-3680 routers that are vulnerable to PixieWPS attack. We though maybes a patch of the firmware has been put in place to prevent this type of attack we began to look online. We found that there has been no mention online about patching except from a lot of community forum users suggesting the vendor to issue a patch back in 2014. Replacements HAWAII Routers where sent to a some customers that have complained or requested replacement hardware also new customers who bought there contracts after 2016 are given HAWAII Routers. But not all customers have been given replacement routers or where informed of any breach of security within there hardware. Many are still left with the notorious vulnerable TalkTalk D-Link DSL-3680 Router. There are still a lot of vulnerable routers our calculations suggest it could be even up to 100,000+ routers in the UK alone.
As a customer who owned one of these routers I was certainly not informed of the vulnerability a patch firmware upgrade or a replacement router and our guess is that they also failed to disclose this vulnerability with many other customers. A lot of notices around the time by news sites and community forums where put out warning about this vulnerability in 2016 but were over looked by a lot of customers as they were not sufficiently informed or even knew about an exploit existing in their Wireless Router.
This opens the question who is responsible for the security of a vulnerable router the ISP or the client or the vendor ?.
How to secure your router
If you own one of these routers D-Link DSL-3680 as pictured above provided by TalkTalk we suggest you take the follow precautions listed below.
Do you really need to use WPS ? WPS can be weak and hold security weakness we recommend turning WPS off on your Wireless Routers.
- First go to your local IP address (192.168.1.1)
- Next goto advanced settings and find the settings for WPS “Turn WPS off”
- Change Routers Password to a secure password
- Change Wi-Fi Pass Code to a secure password
- Be wary of who you trust or what information you are sending over a network as most the time as harsh as it sounds most the time you wont know you have been hacked always be aware.This article is not intended to infringe on any companies but rather as an eye open for customers of Internet based devices to take a deeper look into what they may be buying. We have now come to the end of this article and we hope you all enjoyed it. HackingVision

