WebRTC leak IP address even if you’re behind a VPN Part 2
Welcome back to HackingVision in the last article (WebRTC can leak your IP address even if you’re behind a VPN). we talked a little about WebRTC and STUN servers and how they can affect your privacy online. Today we are going to set up a Web Server and implement a WebRTC Grabber to show proof of concept. our POC is based on WebRTC-IPS & WebRTC Grabber. (Big thanks redpois0n & diafygi for making this proof of concept possible.) WebRTC leak IP
What is WebRTC? WebRTC (Web Real-Time Communication) is a collection of communications protocols and application programming interfaces that enable real-time communication over peer-to-peer connections. This allows web browsers to not only request resources from backend servers, but also real-time information from browsers of other users.
This enables applications such as video conferencing, file transfer, chat, or desktop sharing without the need of either internal or external plugins.
WebRTC is being standardized by the World Wide Web Consortium (W3C) and the Internet Engineering Task Force (IETF). The reference implementation is released as free software under the terms of a BSD license. OpenWebRTC provides another free implementation based on the multimedia framework GStreamer.
WebRTC uses javascript in order to reveal your real IP address. It can make a VPN, Proxy server and services such as Tor (The Onion Router) obsolete by revealing the actual IP address of the VPN user. Since WebRTC uses JavaScript requests to get your IP address, users of NoScript or similar services will not leak their IP addresses.
Requirements:
Web Hosting
PHP
Write permissions in same directory as index.php
Now that we have discussed WebRTC a little we can now proceed to setting up WebRTC-Grabber.
First of all, I will find a free web host and create an account. The web host must support PHP you can get a free web server from 000webhost if you don’t already have hosting.
https://www.000webhost.com/
I have created a domain http://webrtc.unaux.com this will be used to conduct our test.
Now we have web hosting set up. We can now use FTP to upload website files to our webspace. Start an FTP client and connect to your webspace I will use Filezilla.
Once you have connected to your webspace we need to download WebRTC-Grabber you can download WebRTC-Grabber from the following location.
https://github.com/redpois0n/webrtc-grabber
Upload the contents of WebRTC-Grabber to your web hosting space.
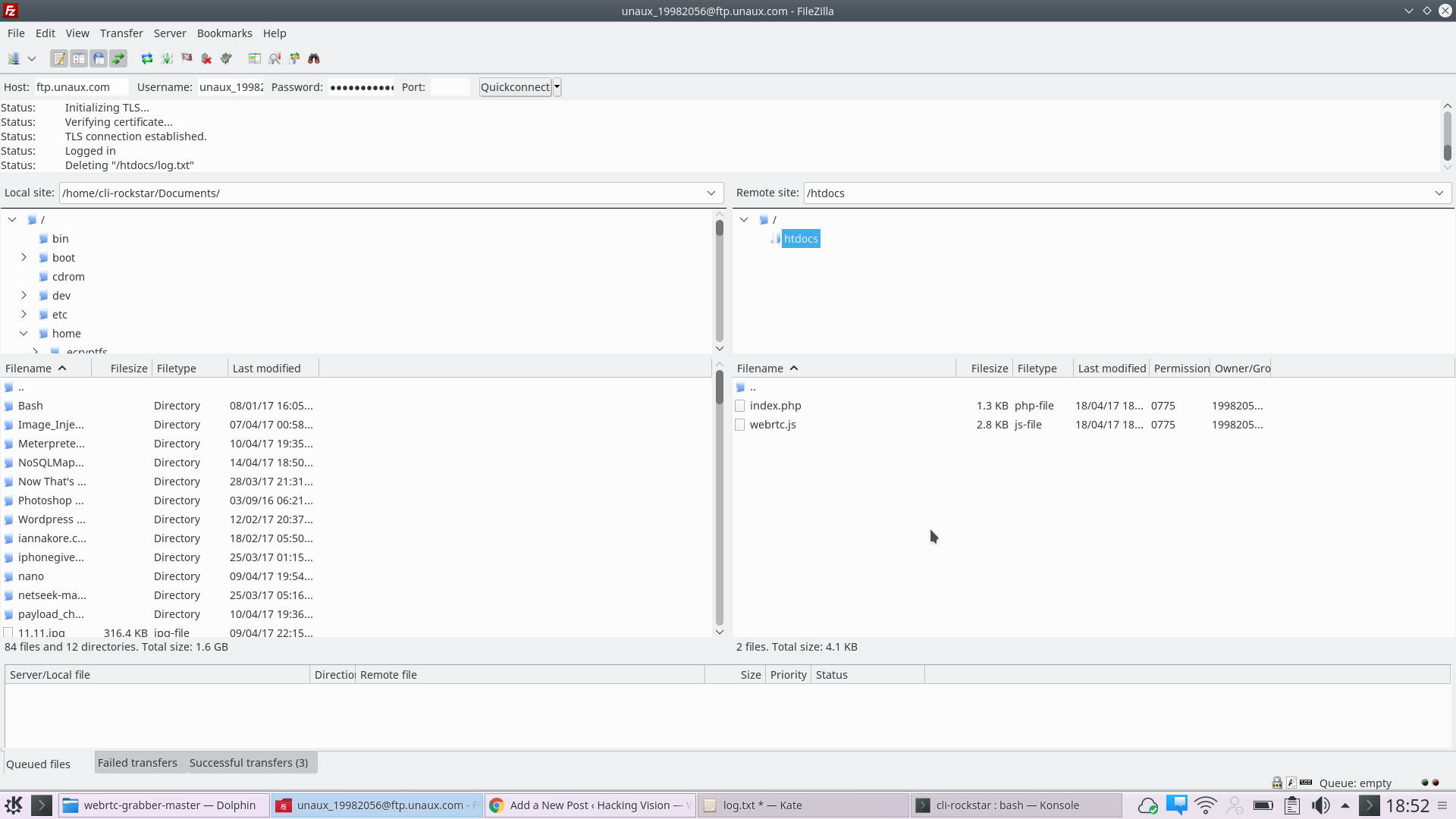
Add Write permissions in same directory as index.php
After WebRTC-Grabber has upload we can now do a quick test.
I will now visit the demo website we set up to conduct our WebRTC test.
As you can see in the screenshot above we now have a new file in our Web Hosting space called log.txt this is where all the logs will be stored. Take a deeper look inside of the log.txt file. we should have successfully captured some IP addresses that have the compatibility of using WebRTC.
If you enjoyed this article please consider sharing it this article was created for educational purposes www.hackingvision.com will not be held responsible for misuse of this information.
Disabling WebRTC
If you enjoyed this article please consider sharing it this article was created for educational purposes www.hackingvision.com will not be held responsible for misuse of this information. We hope you enjoyed our demonstration on how WebRTC leak IP. You can also use https://browserleaks.com/webrtc to check if your actual IP address is being leaked from behind your VPN WebRTC leak IP.