Cracking Password Hashes using Hashcat (Crackstation Wordlist)
Welcome to HackingVision, in this tutorial we will demonstrate how to crack password hashes in Kali Linux with the Crackstation Wordlists.
Hardware
In this tutorial, we are using GTX 1080 8GB and Ryzen 5 1600 CPU in this tutorial you can use whatever NVIDIA GPU that you like. By using both CPU and GPU in Hashcat we can obtain better password hash rates this allows us to crack password hashes faster and more conveniently than we typically could than just using a CPU.
If you’re using a GPU make sure you have the NVIDIA drivers for your GPU installed. If you don’t have access to any NVIDIA GPU a strong CPU is recommended the wordlist we are going to be using is 15 GiB uncompressed Hashcat will take a little while longer if your de-hashing passwords hashes without a GPU. Hash rates will depend on the speed of your computer’s CPU the faster your CPU the better, If you have a fast GPU you will be able to crack passwords much quicker. There are many factors that come into play when it comes to password cracking such as the size of the wordlist, the size of the target hash file and the speed of your CPU or GPU. For example, Dehashing passwords for certain hashing algorithms can be slower than other hashing algorithms. If you are cracking a lot of large password hash lists an SSD is recommended in this guide we are using a standard 1TB HDD currently all of my SSD’s are occupied by other operating systems.
If you have limited bandwidth we can use a Smaller Wordlist that is 684MiB uncompressed but does not include as many passwords or alternatively we can use a wordlist that is included by default in Kali Linux.
Hashes
In this tutorial, we will be de-hashing SHA1 hashes. You can use sha1-online to encrypt SHA1 password hashes. Let’s create some hashes to test with Hashcat.
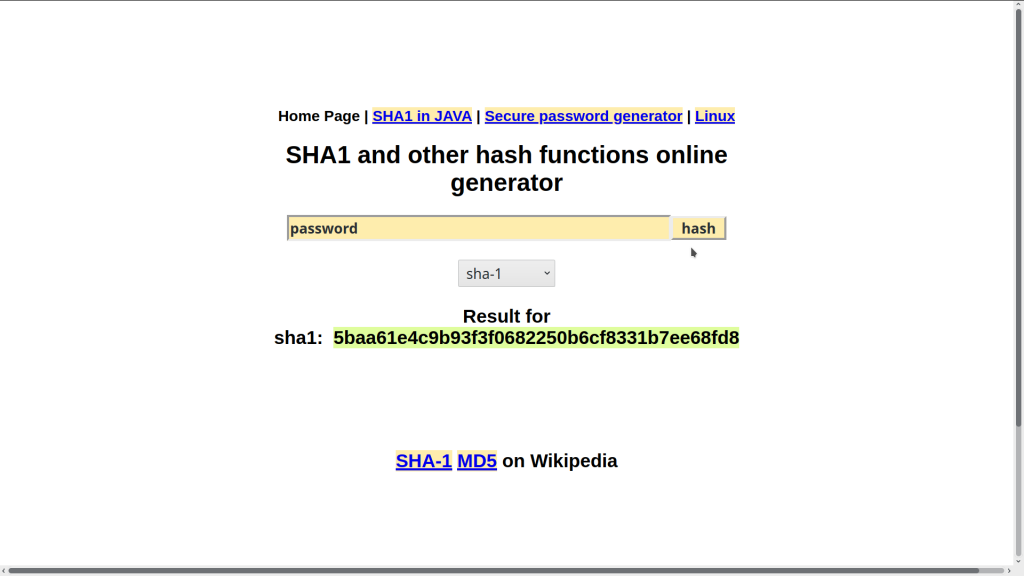
Create some password hashes using sha1-online and save the password hashes hashed by sha1-online into a text file. I will hash 20 passwords and save them in a text file. Create your own password hash list or you can use the password hashes below. I will be using the nano text editor in this tutorial.
Open up a terminal and enter the command. This command will create a new text document called sha1.txt enter your password hashes add each hash byline. You can copy the password hashes below if you don’t want to hash your own password hashes.
nano sha1.txt
36508dc6b91d9e325cb5201c9c3e0f6800a22401 d9a3340fc190666644835cab31417b481e6682cd ddfaa7396a2479971e02adf0782c39a182f606b4 8c8686d62d77eb33cf9d78e016d9383440762dad 90b3b5d2f0c155d50624e0a46be4189d6aa1a63d 28127a006a81ec843d373df2f7b1745a8999c69c e4c0603a123ee10a19cad3782fe9c13e04e89c21 15324d4e8b5cd5f7e5a5e19d7265cadb1d22cd92 9e97bfb1d50fba5f71fe7a9a170cebc21ec00bf8 0ff30704e7b54c009158089bcda81a3be2b0bb19 6c1157276135ca76d64d7a093485d27967368cdb 1723b7c754222f168f6be335878126e144a041c3 c4284a574c1ba187d73da54f9a6fbbc132dde013 226c5895228eba460f38617c3747c9b0b5e138b1 347d5eb7d2dc200a8cd83be2d058712144c25f4d 578b41e68b35d0f088f4b98136abe0835f1fe2bf 7c3607b8e61bcf1944e9e8503a660f21f4b6f3f1 68f4f20202d8b4a2e1ca38f64e384c126eeb1464 eeb01b0a108d74060c494fd67d8a1db39b8f5324 892595270f8609c6602e8721c96249a8dbb7a946
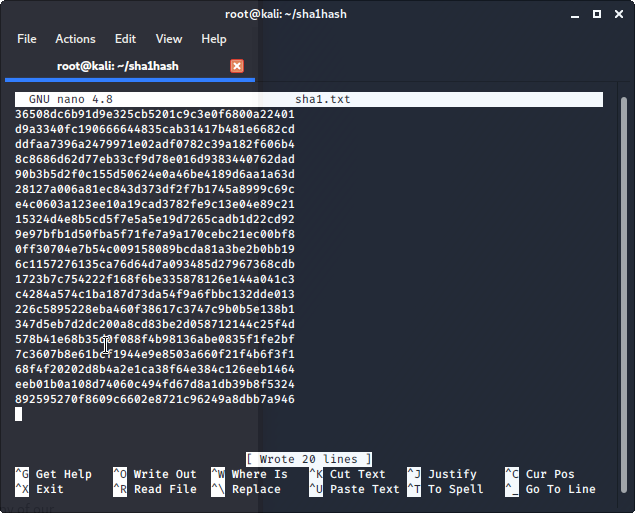
Once you have finished adding your password hashes in nano you can write the file by using keys CTRL+O after changes have been written use CTRL+X to exit the nano text editor.
The passwords that we hashed should be the following when decrypted let’s see if Hashcat can find any of our password hashes.
36508dc6b91d9e325cb5201c9c3e0f6800a22401:cat123 d9a3340fc190666644835cab31417b481e6682cd:StRoNgPaSsWoRd676Secure ddfaa7396a2479971e02adf0782c39a182f606b4:dogcat123 8c8686d62d77eb33cf9d78e016d9383440762dad:rabbitman 90b3b5d2f0c155d50624e0a46be4189d6aa1a63d:suninspain 28127a006a81ec843d373df2f7b1745a8999c69c:englandcup e4c0603a123ee10a19cad3782fe9c13e04e89c21:sha1password 15324d4e8b5cd5f7e5a5e19d7265cadb1d22cd92:BeerDuffBeer 9e97bfb1d50fba5f71fe7a9a170cebc21ec00bf8:BartSimpsonSkate 0ff30704e7b54c009158089bcda81a3be2b0bb19:alienscowboys 6c1157276135ca76d64d7a093485d27967368cdb:8fR&dt 1723b7c754222f168f6be335878126e144a041c3:coffeeortea c4284a574c1ba187d73da54f9a6fbbc132dde013:mouseduck 226c5895228eba460f38617c3747c9b0b5e138b1:computer123 347d5eb7d2dc200a8cd83be2d058712144c25f4d:starwarsguy 578b41e68b35d0f088f4b98136abe0835f1fe2bf:lukeskywalker1 7c3607b8e61bcf1944e9e8503a660f21f4b6f3f1:abcd123 68f4f20202d8b4a2e1ca38f64e384c126eeb1464:seahawk2000 eeb01b0a108d74060c494fd67d8a1db39b8f5324:mysticalfish 892595270f8609c6602e8721c96249a8dbb7a946:no1gamer
Download Wordlist
Download Wordlists: https://crackstation.net/crackstation-wordlist-password-cracking-dictionary.htm

In this tutorial, we will be using Crackstation.txt.gz wordlist. You can choose whatever wordlist you want to use you don’t have to use the crackstation ones that we have included in this tutorial to use Hashcat. We recommend these wordlists as they include lots of leaked real human passwords if you don’t know what the Crackstation wordlists are there the results of Crackstation cracking LinkedIn’s and eHarmony’s password hash leaks with the list.
The wordlist we use using in this tutorial is 4.2GB Compressed and 15 GiB uncompressed (https://crackstation.net/files/crackstation.txt.gz) if you have limited bandwidth use Crackstation Smaller Wordlist (Human Passwords Only) that is 247MiB compressed and 684MiB uncompressed.
Default wordlists in Kali Linux are stored in /usr/share/wordlists
Uncompressing Crackstation Wordlist
To uncompress .txt.gz files we can use gunzip install gzip by opening a terminal and entering the following command. gunzip will uncompress wordlists within the same directory as it’s run from.
apt-get install gzip
Now that gzip is installed we can uncompress the wordlists we downloaded from Crackstaion using the following command.
gunzip crackstation.txt.gz
To uncompress the smaller real human wordlist from crackstation you can use the following command.
gunzip crackstation-human-only.txt.gz
Now that we have uncompressed the Crackstation wordlists we can now use them in Hashcat.
Hashcat
Its time to run Hashcat against our target SHA1 hashes. Let’s see what hashes we can dehash.
Open a terminal
cd into the directory that your hash list is stored in edit the following command -m 100 is hash type SHA1 add the location of your hash list and wordlist.
My hash list is called sha1.txt the output of my passwords.txt file is the same directory as sha1.txt I am using the crackstation wordlist from /usr/share/wordlists/crackstation.txt that I copied to /usr/share/wordlists/ earlier. Your downloaded wordlist is most likely stored and uncompressed in Downloads, in that case, we would add /Downloads/crackstation.txt make sure that you use using the uncompressed wordlist and not the compressed .txt.gz version.
hashcat -m 100 sha1.txt -o passwords.txt /usr/share/wordlists/crackstation.txt
hashcat -m 100 sha1.txt -o passwords.txt /Downloads/crackstation.txt
Command Breakdown -m = hash type SHA1 hashes.txt (your target hashes file goes here) -o passwords.txt = output directory of cracked passwords /usr/share/wordlists/crackstation.txt (Add the path to your wordlist here)
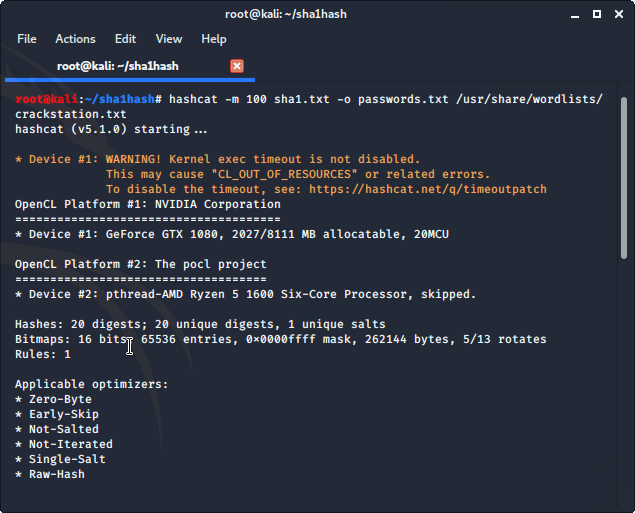
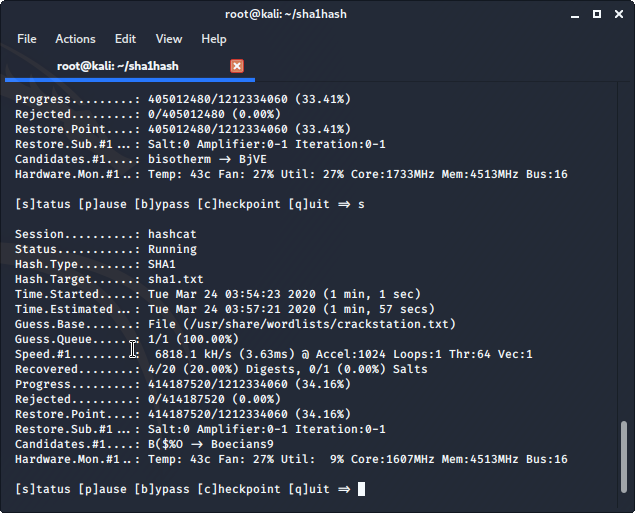
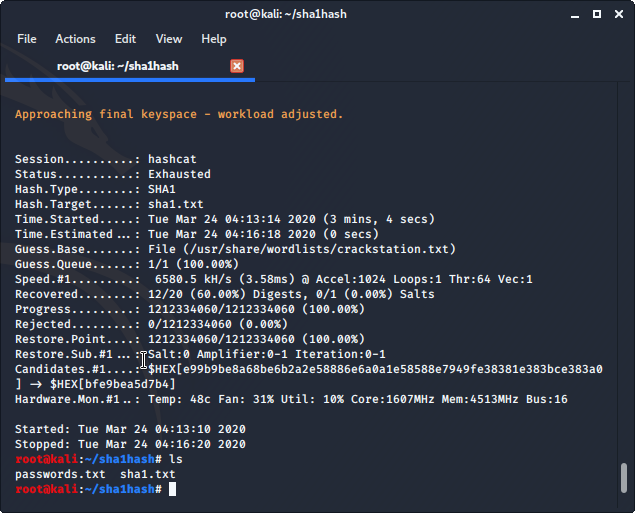
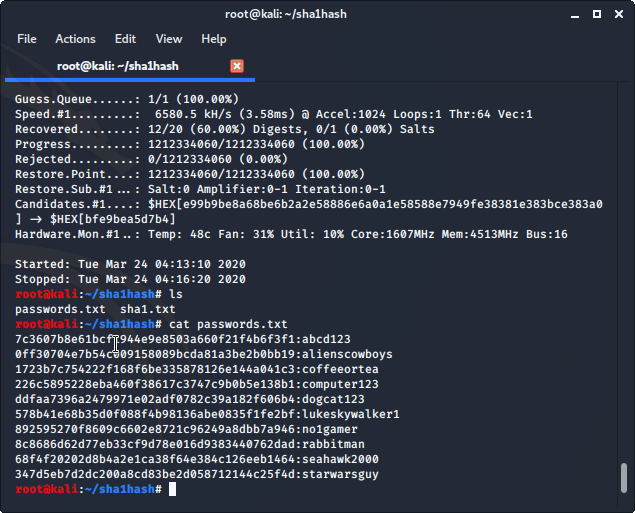
Hashcat found 12/20 password hashes that we gave it using the crackstation.txt wordlist.
Let’s see what passwords Hashcat was able to crack. We can list the contents of the passwords.txt file containing the passwords that Hashcat was able to de-hash using the cat command in Linux.
From the directory that your passwords.txt file is saved in use the following command to list the password words that Hashcat was able to recover. cat is a standard Unix utility that reads files sequentially, writing them to standard output.
cat passwords.txt